312-50 Exam Dumps - Certified Ethical Hacker Exam
Searching for workable clues to ace the ECCouncil 312-50 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s 312-50 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
Which of the following describes the characteristics of a Boot Sector Virus?
Which statement is TRUE regarding network firewalls preventing Web Application attacks?
A large company intends to use Blackberry for corporate mobile phones and a security analyst is assigned to evaluate the possible threats. The analyst will use the Blackjacking attack method to demonstrate how an attacker could circumvent perimeter defenses and gain access to the corporate network. What tool should the analyst use to perform a Blackjacking attack?
An attacker has been successfully modifying the purchase price of items purchased on the company's web site. The security administrators verify the web server and Oracle database have not been compromised directly. They have also verified the Intrusion Detection System (IDS) logs and found no attacks that could have caused this. What is the mostly likely way the attacker has been able to modify the purchase price?
In order to show improvement of security over time, what must be developed?
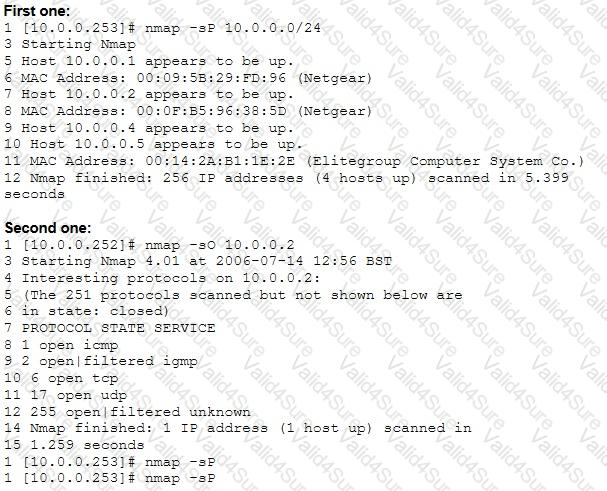
On a Linux device, which of the following commands will start the Nessus client in the background so that the Nessus server can be configured?
ICMP ping and ping sweeps are used to check for active systems and to check