300-710 Exam Dumps - Securing Networks with Cisco Firepower (300-710 SNCF)
Searching for workable clues to ace the Cisco 300-710 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s 300-710 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
Which two statements about deleting and re-adding a device to Cisco FMC are true? (Choose two.)
Refer to the exhibit.
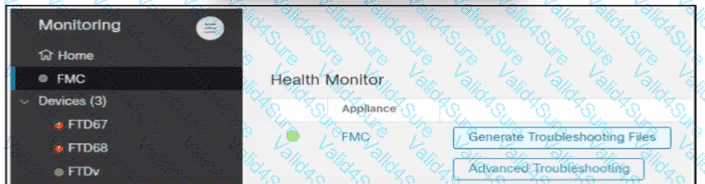
An engineer generates troubleshooting files in Cisco Secure Firewall Management Center (FMC). A successfully completed task Is removed before the files are downloaded. Which two actions must be taken to determine the filename and obtain the generated troubleshooting files without regenerating them? (Choose two.)
What is an advantage of adding multiple inline interface pairs to the same inline interface set when deploying an asynchronous routing configuration?
An organization created a custom application that is being flagged by Cisco Secure Endpoint. The application must be exempt from being flagged. What is the process to meet the requirement?
An engineer must replace a Cisco Secure Firewall high-availability device due to a failure. When the replacement device arrives, the engineer must separate the high-availability pair from Cisco Secure Firewall Management Center Which action must the engineer take first to restore high availability?
An administrator is attempting to add a Cisco Secure Firewall Threat Defence device to Cisco Secure Firewall Management Center with a password of Cisco0480846211 480846211. The private IP address of the FMC server is 192.168.75.201. Which command must be used in order to accomplish this task?
An engineer is configuring a custom application detector for HTTP traffic and wants to import a file that was provided by a third party. Which type of flies are advanced application detectors creates and uploaded as?
What must be implemented on Cisco Firepower to allow multiple logical devices on a single physical device to have access to external hosts?