300-710 Exam Dumps - Securing Networks with Cisco Firepower (300-710 SNCF)
Searching for workable clues to ace the Cisco 300-710 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s 300-710 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
An engineer is configuring a cisco FTD appliance in IPS-only mode and needs to utilize fail-to-wire interfaces. Which interface mode should be used to meet these requirements?
Which policy rule is included in the deployment of a local DMZ during the initial deployment of a Cisco NGFW through the Cisco FMC GUI?
An administrator must use Cisco FMC to install a backup route within the Cisco FTD to route traffic in case of a routing failure with the primary route. Which action accomplishes this task?
What is a limitation to consider when running a dynamic routing protocol on a Cisco FTD device in IRB mode?
A network administrator wants to configure a Cisco Secure Firewall Threat Defense instance managed by Cisco Secure Firewall Management Center to block traffic to known cryptomning networks. Which system settings must the administrator configure in Secure Firewall Management Center to meet the requirement?
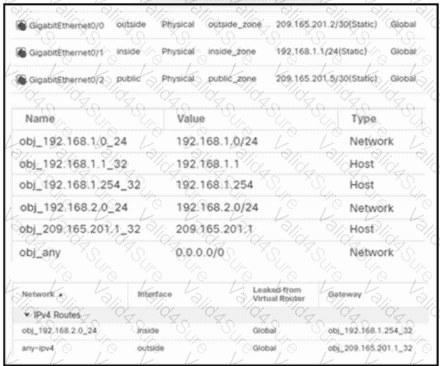
Refer to the exhibit. An engineer configures a NAT rule allowing clients to use the internet only if clients are located on the directly connected internal network. Dynamic auto PAT must be configured. Drag and drop the NAT rules from the left onto the corresponding targets on the right. Not all options are used.

A network engineer detects a connectivity issue between Cisco Secure Firewall Management Centre and Cisco Secure Firewall Threat Defense Initial troubleshooting indicates that heartbeats and events not being received. The engineer re-establishes the secure channels between both peers Which two commands must the engineer run to resolve the issue? (Choose two.)
An engineer is troubleshooting the upgrade of a Cisco Secure Firewall Threat Defense device on the Secure Firewall Management Center 7.0 GUI. The engineer wants to collect the upgrade data and logs. Which two actions must the engineer take? (Choose two.)
 A screenshot of a computer AI-generated content may be incorrect.
A screenshot of a computer AI-generated content may be incorrect.