200-201 Exam Dumps - Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS)
Searching for workable clues to ace the Cisco 200-201 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s 200-201 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
Which step in the incident response process researches an attacking host through logs in a SIEM?
Refer to the exhibit.
An engineer is reviewing a Cuckoo report of a file. What must the engineer interpret from the report?
An engineer receives a security alert that traffic with a known TOR exit node has occurred on the network. What is the impact of this traffic?
Drag and drop the definition from the left onto the phase on the right to classify intrusion events according to the Cyber Kill Chain model.
Refer to the exhibit.
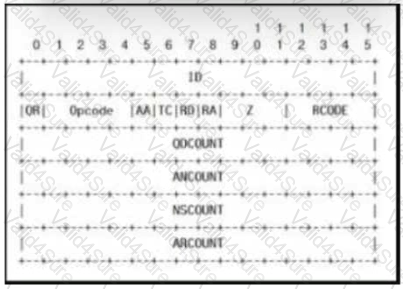
Which field contains DNS header information if the payload is a query or a response?