RH033 Exam Dumps - Red Hat Linux Essentials
Searching for workable clues to ace the RedHat RH033 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s RH033 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
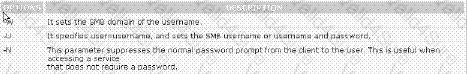
Which of the following commands is used to access Windows resources from Linux workstation?
You work as the Network Administrator for McNeil Inc. The company has a Linux-based network.
You are a root user on the Red Hat operating system. You want to see first five lines of the file
/etc/passwd. Which of the following commands should you use to accomplish the task?
You work as a Network Administrator for Rick International. The company has a Linux-based network. A process is running on a server. It is using a lot of processing power. You want the process to use less resources. Which of the following actions will you perform to accomplish the task?
You work as a Network Administrator for Tech Perfect Inc. The company has a Linux-based network.
There are six files in a directory on your laptop. You want to find out the file types of all the files at a time. Which of the following commands will you use?
Which of the following commands will you run to do case-sensitive search for files named
foobar.png?