PSE-Strata Exam Dumps - Palo Alto Networks System Engineer Professional - Strata
Searching for workable clues to ace the Paloalto Networks PSE-Strata Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s PSE-Strata PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
Which CLI command will allow you to view latency, jitter and packet loss on a virtual SD-WAN interface?
A)
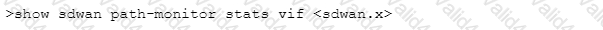
B)
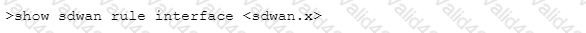
C)

D)

What is the default behavior in PAN-OS when a 12 MB portable executable (PE) fe is forwarded to the WildFire cloud service?
Which Security profile on the Next-Generation Firewall (NGFW) includes Signatures to protect against brute force attacks?
Which proprietary technology solutions will allow a customer to identify and control traffic sources regardless of internet protocol (IP) address or network segment?
What will best enhance security of a production online system while minimizing the impact for the existing network?