NSE6_FML-7.2 Exam Dumps - Fortinet NSE 6 - FortiMail 7.2
Searching for workable clues to ace the Fortinet NSE6_FML-7.2 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s NSE6_FML-7.2 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
Refer to the exhibit, which shows an inbound recipient policy.
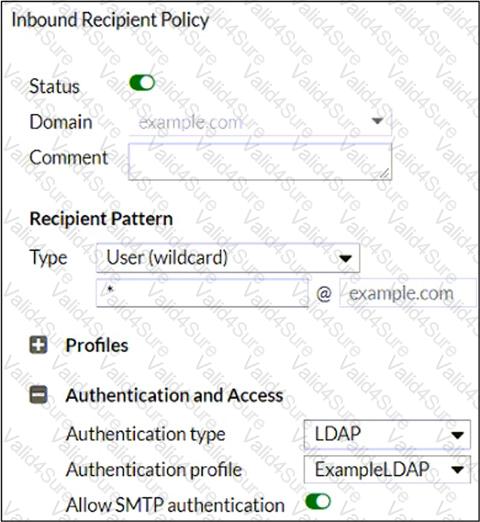
After creating the policy shown in the exhibit, an administrator discovers that clients can send unauthenticated emails using SMTP.
What must the administrator do to enforce authentication?
A FortiMail device is configured with the protected domain example.com.
If none of the senders is authenticated, which two envelope addresses will require an access receive rule? (Choose two.)
Which two features are available when you enable HA centralized monitoring on FortiMail? (Choose two.)
What are two disadvantages of configuring the dictionary and DLP scan rule aggressiveness too high? (Choose two.)
Refer to the exhibit which displays the domain configuration of a transparent mode FortiMail device.
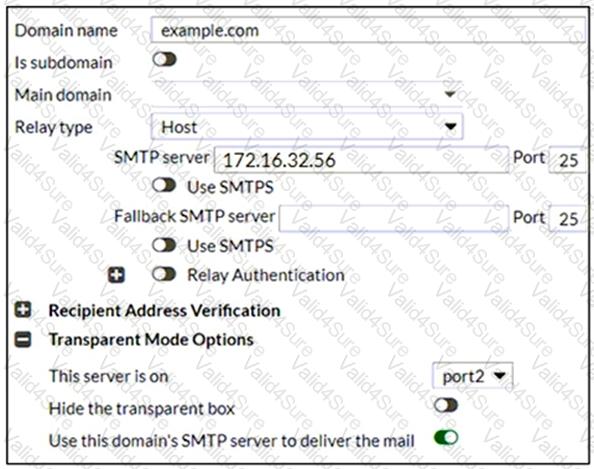
Based on the exhibit, which two sessions are considered incoming sessions? (Choose two.)