NSE5_FAZ-7.2 Exam Dumps - Fortinet NSE 5 - FortiAnalyzer 7.2
Searching for workable clues to ace the Fortinet NSE5_FAZ-7.2 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s NSE5_FAZ-7.2 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
In the FortiAnalyzer FortiView, source and destination IP addresses from FortiGate devices arenotresolving to a hostname.
How can you resolve the source and destination IP addresses, without introducing any additional performance impact to FortiAnalyzer?
What happens when a log file saved on FortiAnalyzer disks reaches the size specified in the device log
settings?
Refer to the exhibit.
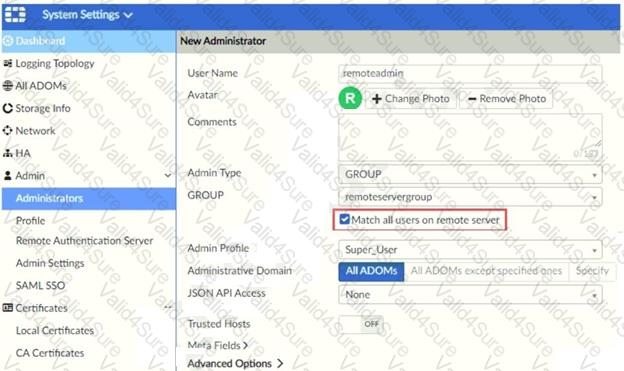
The exhibit shows “remoteservergroup†is an authentication server group with LDAP and RADIUS servers.
Which two statements express the significance of enabling “Match all users on remote server†when configuring a new administrator? (Choose two.)
Refer to the exhibits.
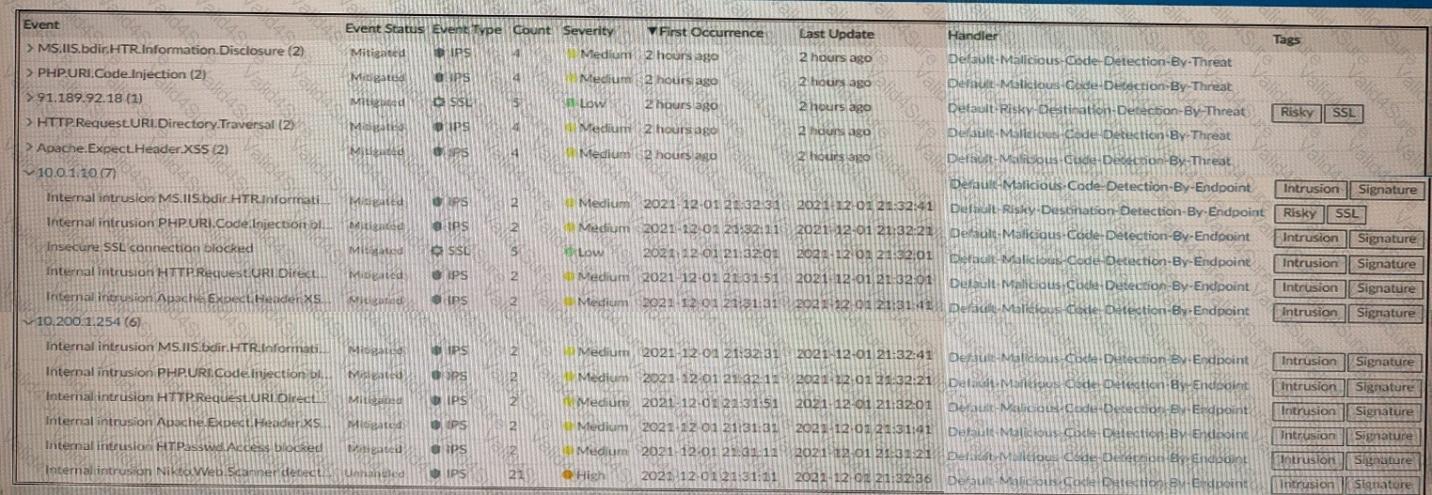
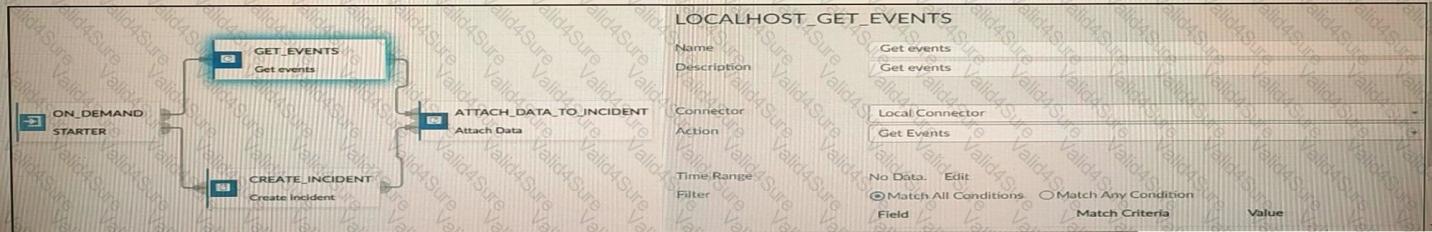
How many events will be added to the incident created after running this playbook?