NSE4_FGT_AD-7.6 Exam Dumps - Fortinet NSE 4 - FortiOS 7.6 Administrator
Searching for workable clues to ace the Fortinet NSE4_FGT_AD-7.6 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s NSE4_FGT_AD-7.6 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
Refer to the exhibit.
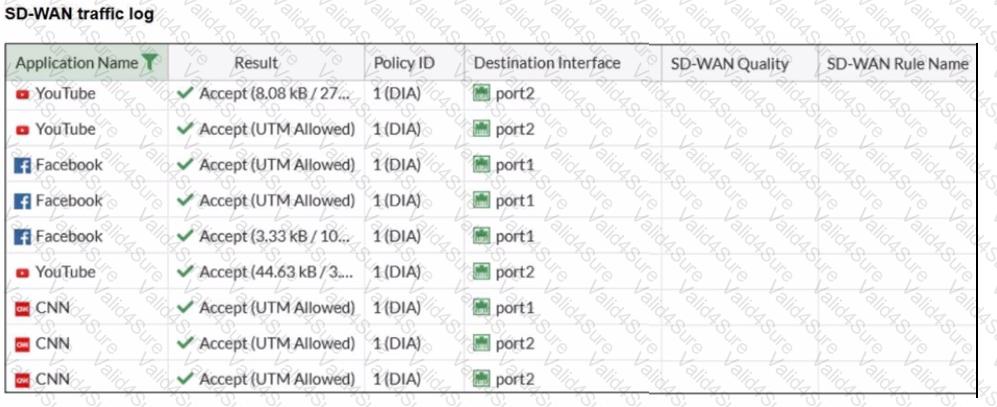
The administrator configured SD-WAN rules and set the FortiGate traffic log page to display SD-WAN-specific columns: SD-WAN Quality and SD-WAN Rule Name
FortiGate allows the traffic according to policy ID 1 placed at the top. This is the policy that allows SD-WAN traffic. Despite these settings, the traffic logs do not show the name of the SD-WAN rule used to steer those traffic flows
What could be the reason?
You have configured an application control profile, set peer-to-peer traffic to Block under the Categories tab. and applied it to the firewall policy. However, your peer-to-peer traffic on known ports is passing through the FortiGate without being blocked.
What FortiGate settings should you check to resolve this issue?
Refer to the exhibits.
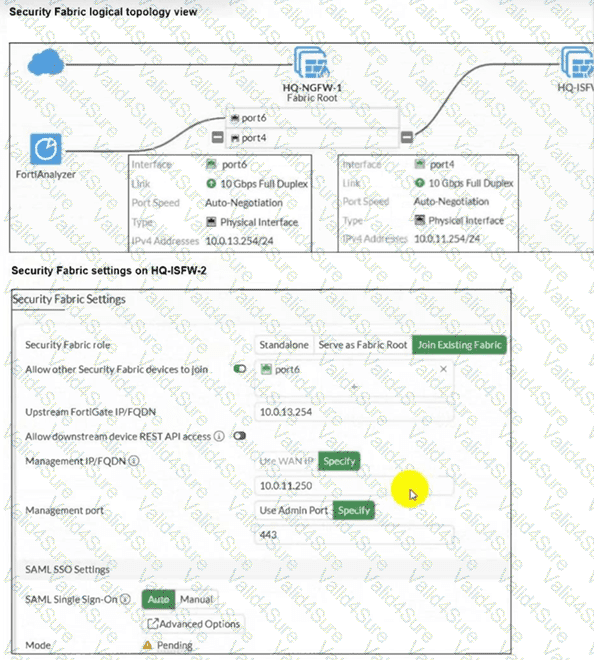
An administrator wants to add HQ-ISFW-2 in the Security Fabric. HQ-ISFW-2 is in the same subnet as HQ-ISFW. After configuring the Security Fabric settings on HQ-ISFW-2, the status stays Pending. What can be the two possible reasons? (Choose two answers)
Refer to the exhibit
A firewall policy to enable active authentication is shown.
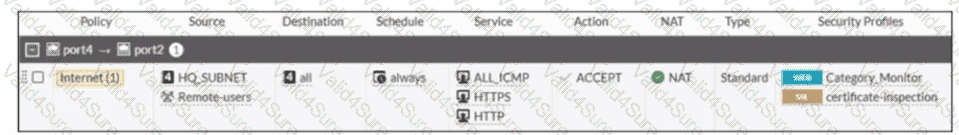
When attempting to access an external website using an active authentication method, the user is not presented with a login prompt. What is the most likely reason for this situation?
Which statement correctly describes NetAPI polling mode for the FSSO collector agent?
Which two statements describe characteristics of automation stitches? (Choose two answers)
Refer to the exhibit.
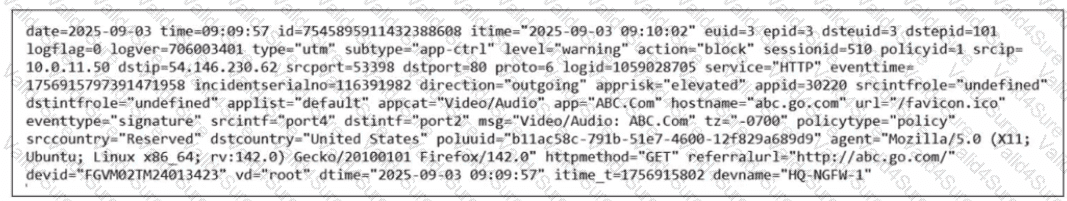
Which two ways can you view the log messages shown in the exhibit? (Choose two.)
You have configured the below commands on a FortiGate.
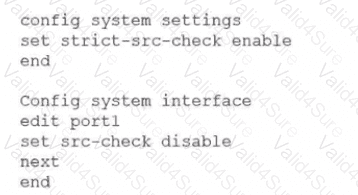
What would be the impact of this configuration on FortiGate?