NCS-Core Exam Dumps - Nutanix Certified Services Core Infrastructure Professional (NCS-Core 6.8)
Searching for workable clues to ace the Nutanix NCS-Core Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s NCS-Core PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
Refer to the exhibit.
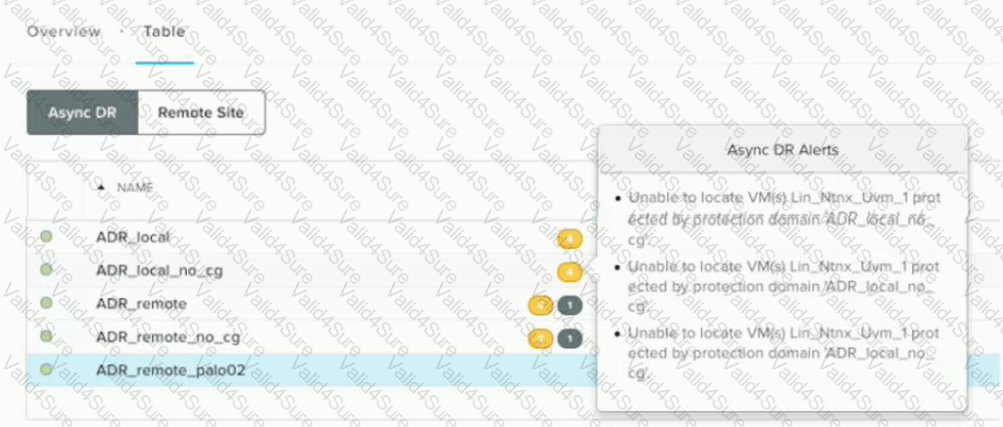
After performing ESXi to AHV conversion on a cluster, the alerts shown in the exhibit display on Prism. What should the administrator do to resolve this issue efficiently?
After a consultant runs a bare metal Foundation, the imaging process fails.
In which two locations can the consultant find the logs? (Choose two.)
A new Nutanix cluster is ready for production on a remote site with no IT staff. Changes to the infrastructure will cost money and probably cause a cluster stop. The administrator needs to perform a health check on the environment that should include:
• Network connectivity checks
• Network performance status
• Storage performance status
Which tool should be used to perform this test?
Which two components must be identified to validate that software compatibility requirements are met for Nutanix Cluster Installation? (Choose two.)