MS-500 Exam Dumps - Microsoft 365 Security Administration
You have a Microsoft 365 tenant that uses Azure Information Protection to encrypt sensitive content.
You plan to implement Microsoft Cloud App Security to inspect protected files that are uploaded to Microsoft OneDrive for Business.
You need to ensure that at Azure Information Protection-protected files can be scanned by using Cloud App Security
Which two actions should you perform7 Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
You have a Microsoft 365 ES subscription that contains a Microsoft SharePoint Online site named Site1. You create an information barrier segment named Segment 1. You need to add Segment 1 to Site1. What should you do first?
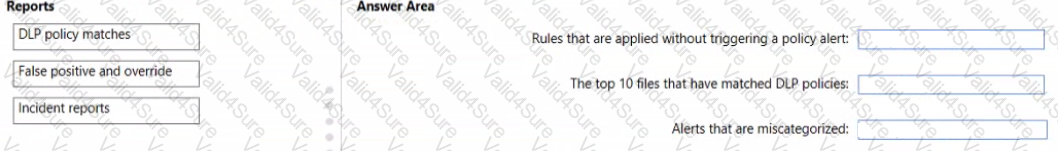
You have a Microsoft 365 subscription that contains 20 data loss prevention (DLP) policies.
You need to identify the following:
• Rules that are applied without Triggering a policy alert
• The top 10 files that have matched DLP policies
• Alerts that are miscategorized
Which report should you use for each requirement? To answer, drag the appropriate reports to the correct requirements. Each report may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
You have a Microsoft 365 subscription.
You enable auditing for the subscription.
You plan to provide a user named Auditor with the ability to review audit logs.
You add Auditor to the Global administrator role group.
Several days later, you discover that Auditor disabled auditing.
You remove Auditor from the Global administrator role group and enable auditing.
- Be prevented from disabling auditing
- Use the principle of least privilege
- Be able to review the audit log
To which role group should you add Auditor?
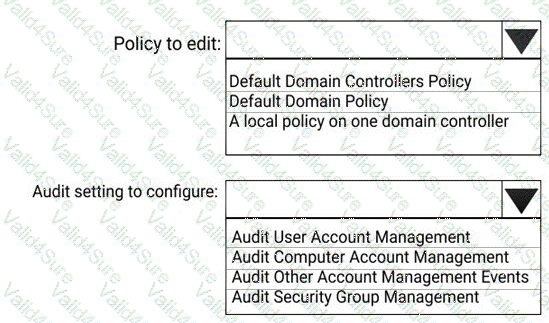
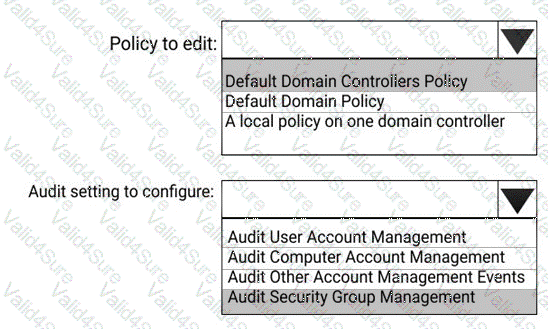
You install Azure ATP sensors on domain controllers.
You add a member to the Domain Admins group. You view the timeline in Azure ATP and discover that information regarding the membership change is missing.
You need to meet the security requirements for Azure ATP reporting.
What should you configure? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.