HPE6-A73 Exam Dumps - Aruba Certified Switching Professional Exam
Searching for workable clues to ace the HP HPE6-A73 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s HPE6-A73 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
Examine the following AOS-CX switch configuration:
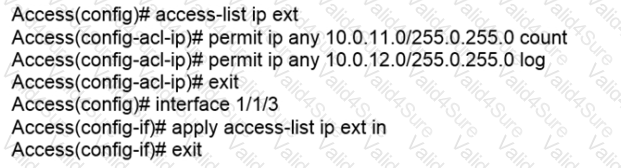
Which statement correctly describes what is allowed for traffic entering interface 1/1/3?
An administrator is managing a network comprised of AOS-CX switches deployed at the aggregation layer. The switches are paired in a VSX stack and run the OSPF routing protocol. The administrator is concerned about how long it takes for OSPF to converge when one of the VSX switches has to reboot.
What should the administrator to do speed up the OSPF convergence of the switch that is rebooting?
Examine the network exhibit:
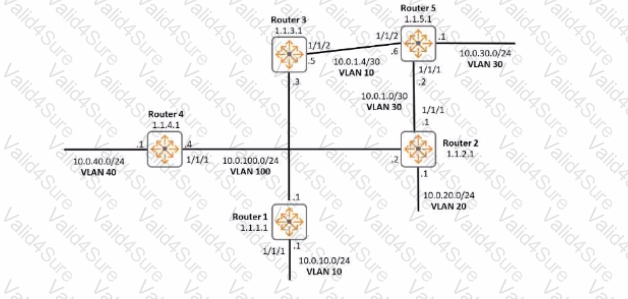
Examine Rome r4"s partial OSPF configuration: router OSPF 1
Area 0
exit interface vlan 100
ip ospf area 0
exit interface vlan 40
ip ospf area 0
exit interface 1/1/1
vlan access 100
mtu9000
Ip ospt hello-Interval 1
Ip ospt dead-Interval 4
ip ospf authentication simple-text
ip ospf authentication-key key123
When executing the "show ip ospf neighbors" command, Router 4 is in a FULL state with Router 3 and Router 2, but a 2-WAY state with Route3. What is causing the 2-WAY state with Router 1?
What would prevent two OSPF routers from forming an adjacency? (Select two.)
What is correct regarding rate limiting and egress queue shaping on AOS-CX switches?