H12-891_V1.0 Exam Dumps - HCIE-Datacom V1.0
Searching for workable clues to ace the Huawei H12-891_V1.0 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s H12-891_V1.0 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
AH is an IP-based transport-layer protocol. The protocol number is _____. (Enter only digits.)
A client sends an HTTP request to a server, and the server sends back an HTTP response. Which of the following parameters isnotcarried in the HTTP response?
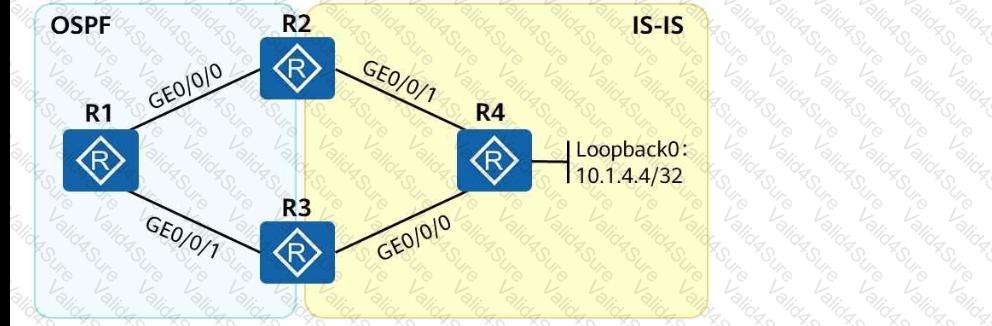
As shown in the following figure, an engineer tests network interconnection between two branches. To implement network interconnection,OSPFis deployed onR1, R2, and R3of branch 1, andIS-ISis deployed onR2, R3, and R4of branch 2. Which of the following operations needs to be performed to allowR1 to access R4's loopback interface address?
In the following figure, OSPF is enabled on all router interfaces. The IP addresses marked in the figure belong to Loopback0 of the routers.
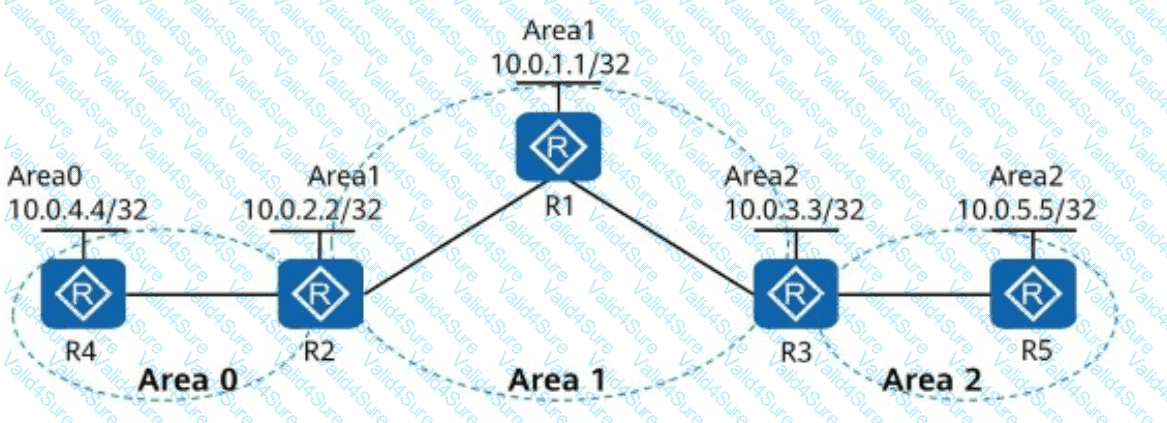
The Loopback0 addresses of R1 and R2 are advertised in Area 1, the Loopback0 address of R4 is advertised in Area 0, and the Loopback0 addresses of R3 and R5 are advertised in Area 2. Given this, which of the following IP addresses can ping each other?
As shown in the following figure, OSPF is deployed on a campus network to implement network interconnection, and Area 1 is deployed as an NSSA. To enable R1 to access R4’s loopback interface address, an engineer imports a direct route to R4’s OSPF process. Which of the following statements about this scenario are correct?
[R4-ospf-1] import-route direct
Loopback0: 10.1.4.4/32
Which of the following statements are correct about authentication points and policy enforcement points in Huawei's free mobility solution?
At the NETCONF content layer, the
In the admission design for large- and medium-sized campus networks, which of the following authentication modes can be used for PCs connected to IP phones?