H12-721 Exam Dumps - Huawei Certified ICT Professional - Constructing Infrastructure of Security Network
Searching for workable clues to ace the Huawei H12-721 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s H12-721 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
The ip-link sends a probe packet to the specified IP address. By default, after 3 probe failures, the link to this IP address is considered faulty.
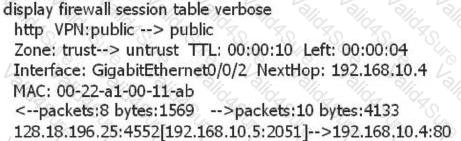
Based on the following information analysis on the firewall, which of the following options are correct?
DDoS is an abnormal packet that an attacker sends a small amount of non-traffic traffic to the attack target (usually a server, such as DNS or WEB) through the network, so that the attacked server resolves the packet when the system crashes or the system is busy.
About load balancing, the following configuration is available: [USG] slb enable [USG]slb [USG-slb] rserver 1 rip 10.1.1.3 weight 32 [USG-slb] rserver 2 rip 10.1.1.4 weight 16 [USG-slb] rserver 3 rip 10.1.1.5 weight 32 [USG-slb] group test [USG-slb-group-test]metric srchash [USG-slb-group-test] add rserver 1 [USG-slb-group-test] add rserver 2 [ USG-slb-group-test] add rserver 3 Which of the following statements is correct?
The management control information and service information of the out-of-band management interface are sent on the same channel.