FCSS_EFW_AD-7.6 Exam Dumps - Fortinet NSE 7 - Enterprise Firewall 7.6 Administrator
Searching for workable clues to ace the Fortinet FCSS_EFW_AD-7.6 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s FCSS_EFW_AD-7.6 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
An administrator received a FortiAnalyzer alert that a 1 ТВ disk filled up in a day. Upon investigation, they found thousands of unusual DNS log requests, such as JHCMQK.website.com, with no answers. They later discovered that DNS exfiltration was occurring through both UDP and TLS.
How can the administrator prevent this data theft technique?
A user reports that their computer was infected with malware after accessing a secured HTTPS website. However, when the administrator checks the FortiGate logs, they do not see that the website was detected as insecure despite having an SSL certificate and correct profiles applied on the policy.
How can an administrator ensure that FortiGate can analyze encrypted HTTPS traffic on a website?
Refer to the exhibit, which contains a partial command output.

The administrator has configured BGP on FortiGate. The status of this new BGP configuration is shown in the exhibit.
What configuration must the administrator consider next?
An administrator configured the FortiGate devices in an enterprise network to join the Fortinet Security Fabric. The administrator has a list of IP addresses that must be blocked by the data center firewall. This list is updated daily.
How can the administrator automate a firewall policy with the daily updated list?
Refer to the exhibit, which shows an ADVPN network.
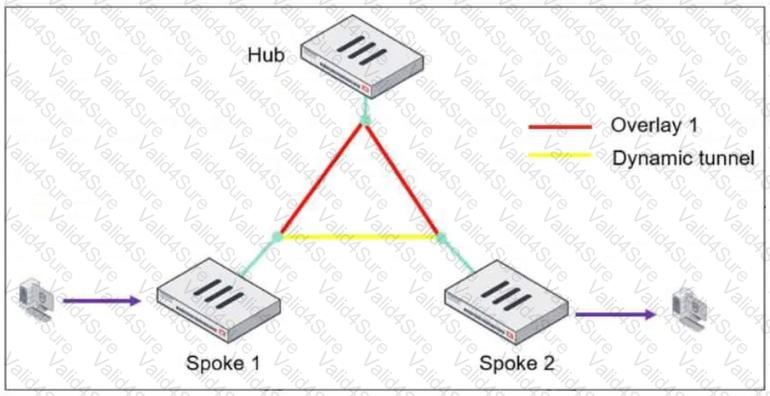
The client behind Spoke-1 generates traffic to the device located behind Spoke-2.
What is the first message that the hub sends to Spoke-1 to bring up the dynamic tunnel?
Refer to the exhibit.
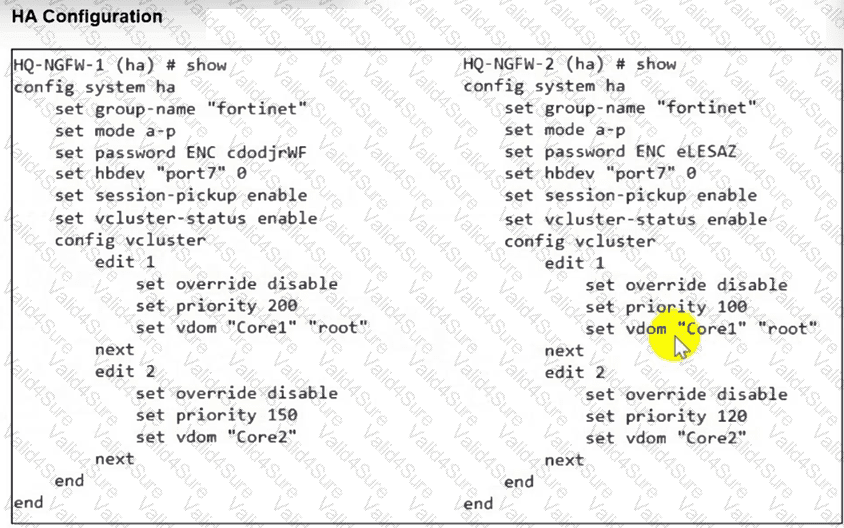
An HA configuration of an active-active (A-A) cluster with the same HA uptime is shown. You want HQ-NGFW-2 to handle the Core2 VDOM traffic. Which modification must you make to achieve this outcome? (Choose one answer)
An administrator is extensively using VXLAN on FortiGate.
Which specialized acceleration hardware does FortiGate need to improve its performance?
An administrator applied a block-all IPS profile for client and server targets to secure the server, but the database team reported the application stopped working immediately after.
How can an administrator apply IPS in a way that ensures it does not disrupt existing applications in the network?
 A client behind Spoke-1 sends traffic to a device behind Spoke-2.
A client behind Spoke-1 sends traffic to a device behind Spoke-2. The traffic initially flows through the hub, following the pre-established overlay tunnel.
The traffic initially flows through the hub, following the pre-established overlay tunnel. The hub detects that Spoke-1 is communicating with Spoke-2 and determines that a direct shortcut tunnel between the spokes can optimize the connection.
The hub detects that Spoke-1 is communicating with Spoke-2 and determines that a direct shortcut tunnel between the spokes can optimize the connection. The hub sends a "Shortcut Offer" message to Spoke-1, informing it that a direct dynamic tunnel to Spoke-2 is possible.
The hub sends a "Shortcut Offer" message to Spoke-1, informing it that a direct dynamic tunnel to Spoke-2 is possible. Spoke-1 and Spoke-2 then negotiate and establish a direct IPsec tunnel for communication.
Spoke-1 and Spoke-2 then negotiate and establish a direct IPsec tunnel for communication.