Deep-Security-Professional Exam Dumps - Trend Micro Certified Professional for Deep Security Exam
Searching for workable clues to ace the Trend Micro Deep-Security-Professional Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s Deep-Security-Professional PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
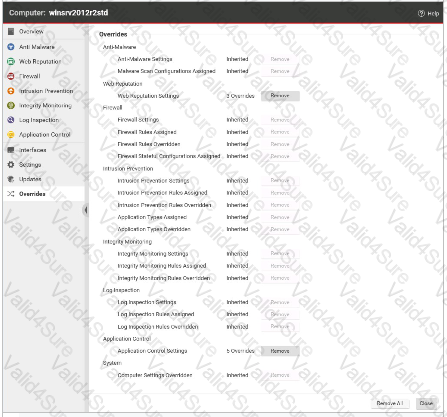
The Overrides settings for a computer are displayed in the exhibit. Which of the following statements is true regarding the displayed configuration?
The Intrusion Prevention Protection Module is enabled, but the traffic it is trying to analyze is encrypted through https. How is it possible for the Intrusion Prevention Protection Module to monitor this encrypted traffic against the assigned rules?
Which Deep Security Protection Modules can be used to provide runtime protection for the Kubernetes and Docker platforms? Select all that apply.
The Intrusion Prevention Protection Module is enabled, its Behavior is set to Prevent and rules are assigned. When viewing the events, you notice that one of Intrusion Prevention rules is being triggered and an event is being logged but the traffic is not being blocked. What is a possible reason for this?