CTAL-TTA Exam Dumps - Certified Tester Advanced Level Technical Test Analyst
Searching for workable clues to ace the ISTQB CTAL-TTA Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s CTAL-TTA PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
Which of the following does NOT contribute to a more effective review preparation by the Technical Test Analyst?
A new system is being built to handle the message handling of financial transactions - this system is critical to the organization's finances. The code includes loops and decisions with several multiple conditions. The nature of the system means that tests are quite time-consuming to execute. Which of the following would be the BEST white box testing option for the new software?
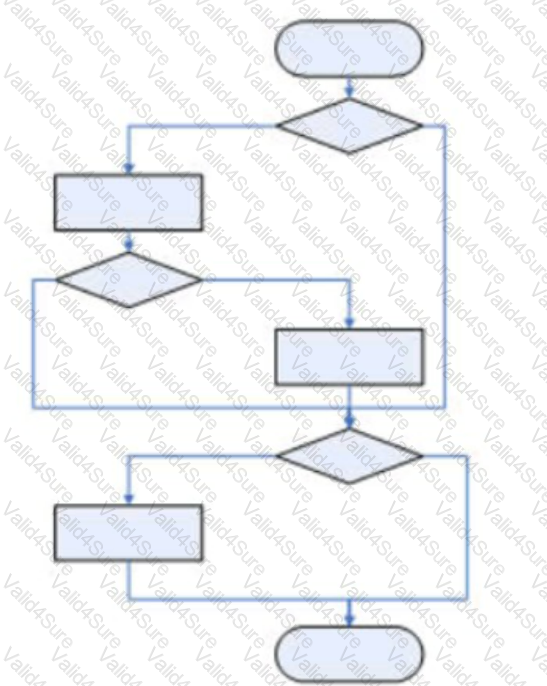
Consider the simplified logic below for crediting money to a bank account.
Receive money and account number to be credited
IF account number is valid
IF customer account is active
Store current account balance as oldBalance
Credit money to account
IF oldBalance < zero
IF balance now >= zero
Set message "Overdraft cleared"
ELSE
Set message "A/c overdrawn"
ENDIF
ELSE
Set message = "You have more money"
ENDIF
IF account holder is VIP customer
Send message by email to customer
ENDIF
ELSE
Set message "A/c inactive"
Send message by email to supervisor
ENDIF
ELSE
Add 1 to count of invalid inputs
ENDIF
What is the minimum quantity of test cases that will give 100% statement coverage?
Which of the following statements is true regarding fault seeding and fault injection tools?