CS0-003 Exam Dumps - CompTIA CyberSecurity Analyst CySA+ Certification Exam
Searching for workable clues to ace the CompTIA CS0-003 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s CS0-003 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
A company recently experienced a security incident. The security team has determined
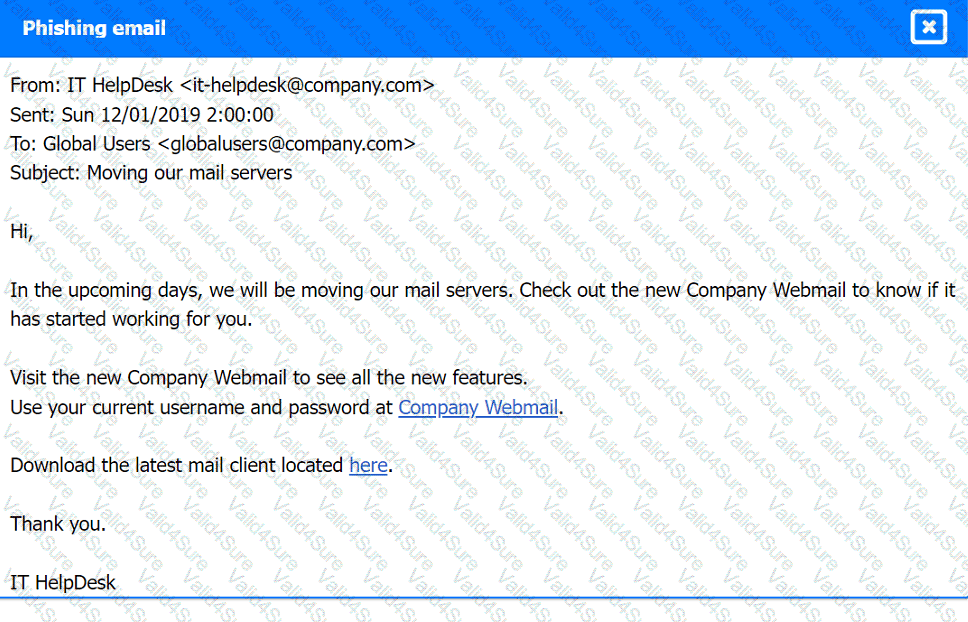
a user clicked on a link embedded in a phishing email that was sent to the entire company. The link resulted in a malware download, which was subsequently installed and run.
INSTRUCTIONS
Part 1
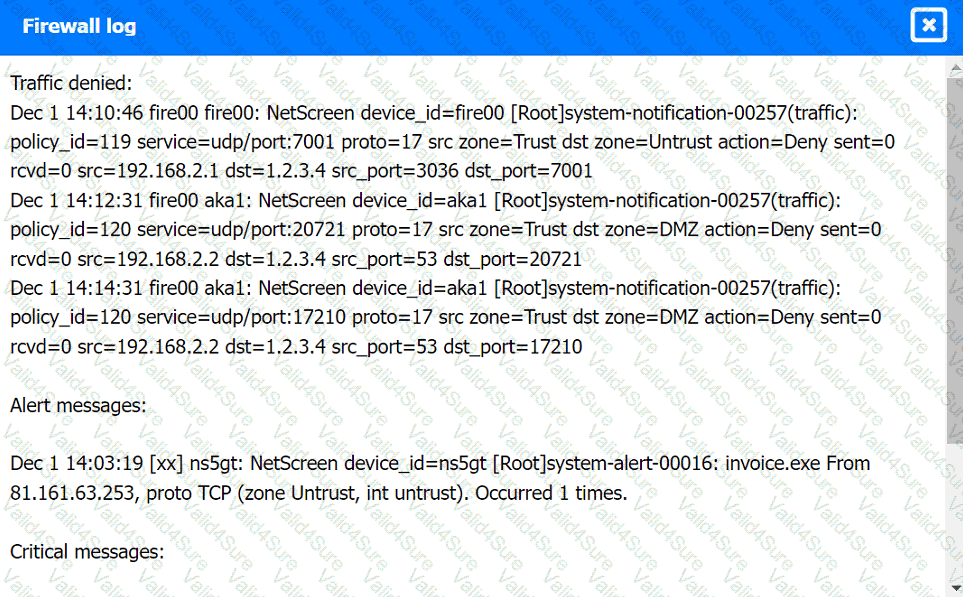
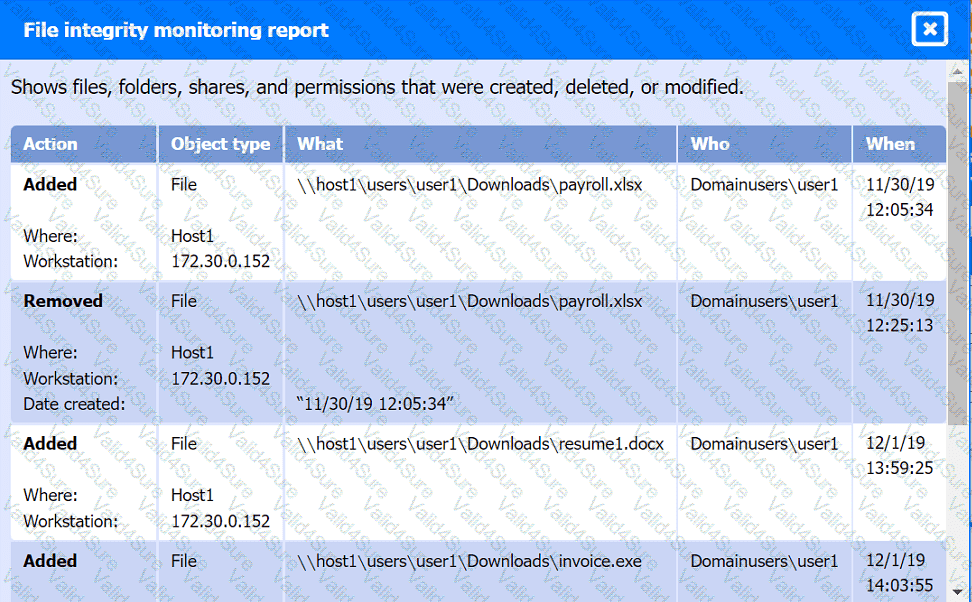
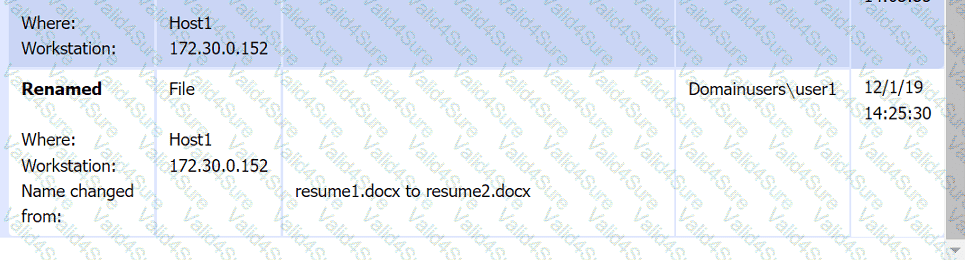
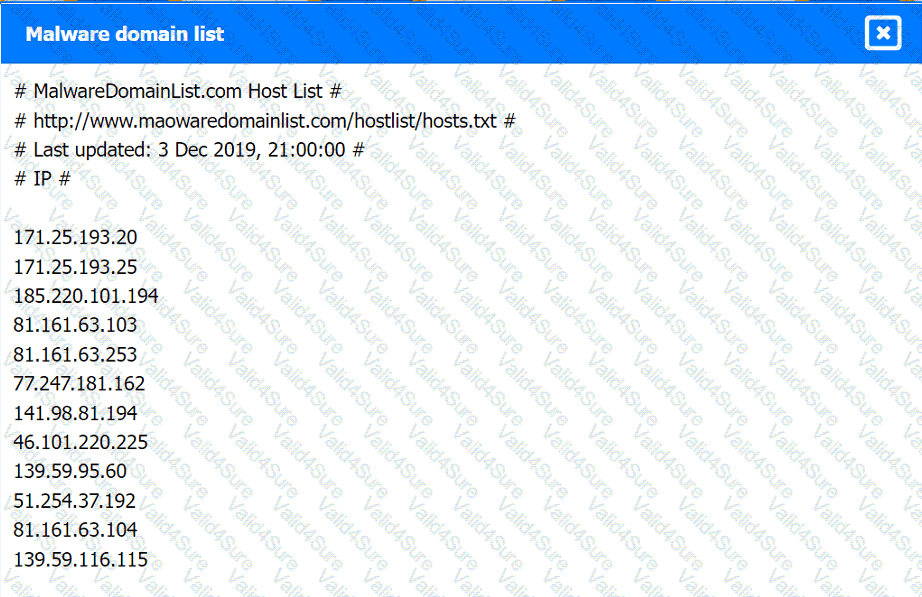
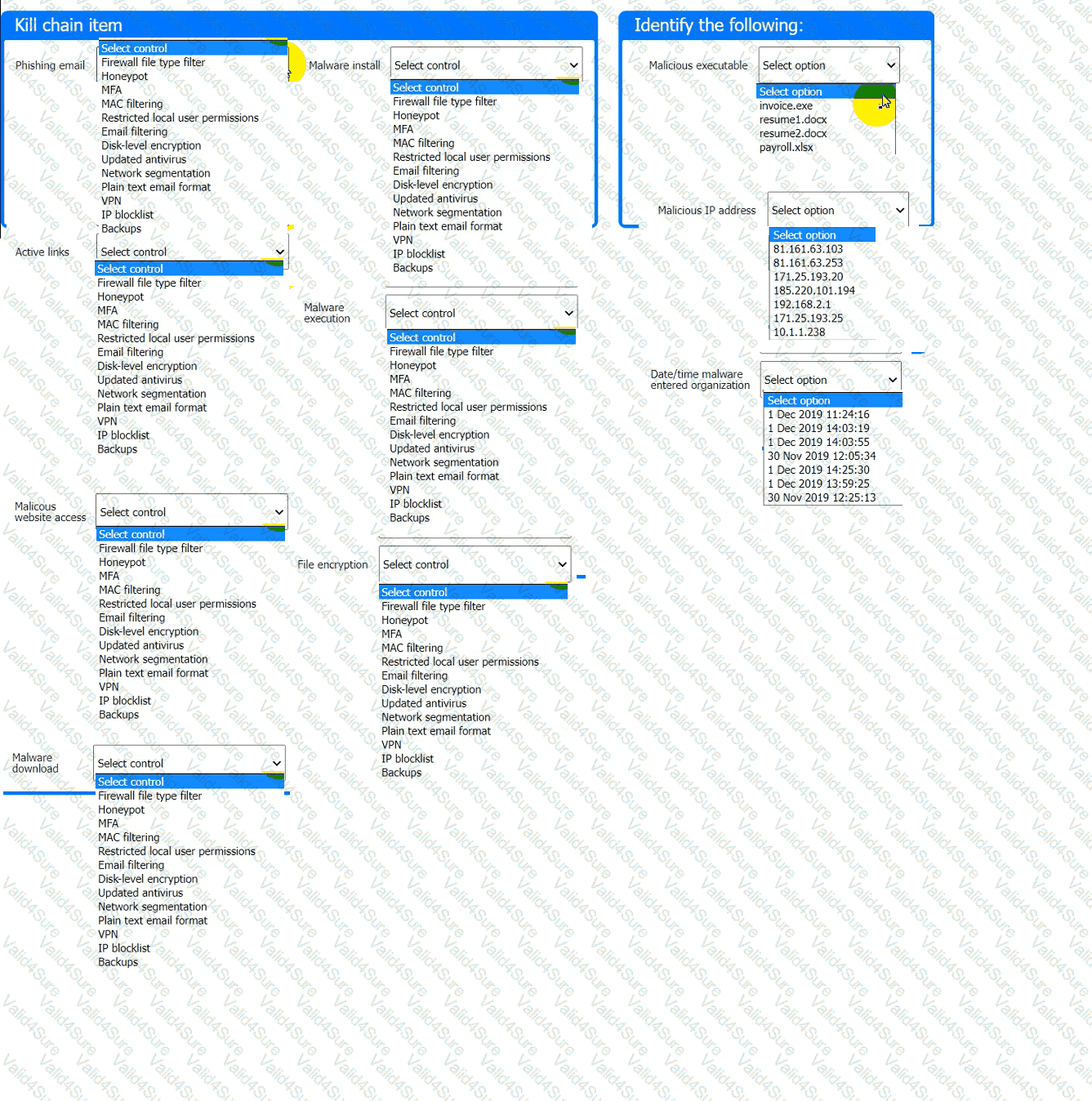
Review the artifacts associated with the security incident. Identify the name of the malware, the malicious IP address, and the date and time when the malware executable entered the organization.
Part 2
Review the kill chain items and select an appropriate control for each that would improve the security posture of the organization and would have helped to prevent this incident from occurring. Each
control may only be used once, and not all controls will be used.
Firewall log:

File integrity Monitoring Report:
Malware domain list:
Vulnerability Scan Report:


Phishing Email:
An attacker has just gained access to the syslog server on a LAN. Reviewing the syslog entries has allowed the attacker to prioritize possible next targets. Which of the following is this an example of?
A security manager is looking at a third-party vulnerability metric (SMITTEN) to improve upon the company's current method that relies on CVSSv3. Given the following:
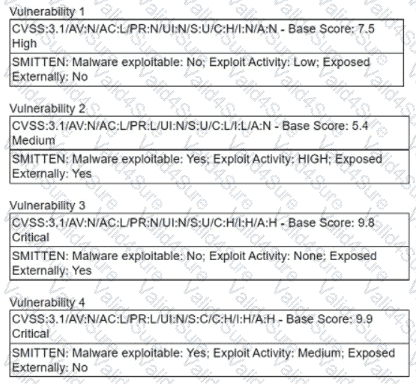
Which of the following vulnerabilities should be prioritized?
An IT professional is reviewing the output from the top command in Linux. In this company, only IT and security staff are allowed to have elevated privileges. Both departments have confirmed they are not working on anything that requires elevated privileges. Based on the output below:
PID
USER
VIRT
RES
SHR
%CPU
%MEM
TIME+
COMMAND
34834
person
4980644
224288
111076
5.3
14.44
1:41.44
cinnamon
34218
person
51052
30920
23828
4.7
0.2
0:26.54
Xorg
2264
root
449628
143500
26372
14.0
3.1
0:12.38
bash
35963
xrdp
711940
42356
10560
2.0
0.2
0:06.81
xrdp
Which of the following PIDs is most likely to contribute to data exfiltration?
Which of the following best describes the key goal of the containment stage of an incident response process?
A SOC manager reviews metrics from the last four weeks to investigate a recurring availability issue. The manager finds similar events correlating to the times of the reported issues.
Which of the following methods would the manager most likely use to resolve the issue?
A security analyst is reviewing the following alert that was triggered by FIM on a critical system:
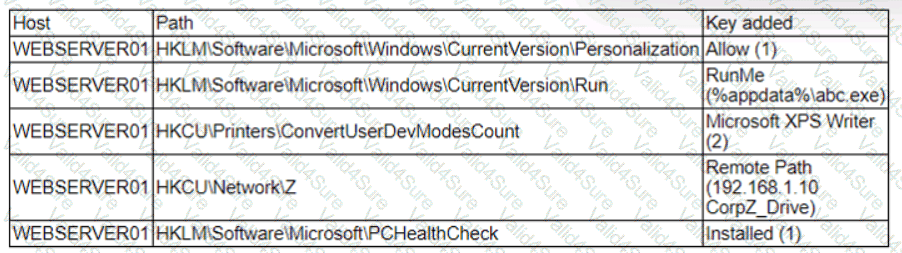
Which of the following best describes the suspicious activity that is occurring?
A security analyst reviews a SIEM alert related to a suspicious email and wants to verify the authenticity of the message:
SPF = PASS
DKIM = FAIL
DMARC = FAIL
Which of the following did the analyst most likely discover?