CS0-003 Exam Dumps - CompTIA CyberSecurity Analyst CySA+ Certification Exam
Searching for workable clues to ace the CompTIA CS0-003 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s CS0-003 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
A company receives a penetration test report summary from a third party. The report summary indicates a proxy has some patches that need to be applied. The proxy is sitting in a rack and is not being
used, as the company has replaced it with a new one. The CVE score of the vulnerability on the proxy is a 9.8. Which of the following best practices should the company follow with this proxy?
During an internal code review, software called "ACE" was discovered to have a vulnerability that allows the execution of arbitrary code. The vulnerability is in a legacy, third-party vendor resource that is used by the ACE software. ACE is used worldwide and is essential for many businesses in this industry. Developers informed the Chief Information Security Officer that removal of the vulnerability will take time. Which of the following is the first action to take?
A security analyst is investigating an unusually high volume of requests received on a web server. Based on the following command and output:
access_log - [21/May/2024 13:19:06] "GET /newyddion HTTP/1.1" 404 -
access_log - [21/May/2024 13:19:06] "GET /1970 HTTP/1.1" 404 -
access_log - [21/May/2024 13:19:06] "GET /dopey HTTP/1.1" 404 -
...
Which of the following best describes the activity that the analyst will confirm?
An analyst suspects cleartext passwords are being sent over the network. Which of the following tools would best support the analyst's investigation?
A company classifies security groups by risk level. Any group with a high-risk classification requires multiple levels of approval for member or owner changes. Which of the following inhibitors to remediation is the company utilizing?
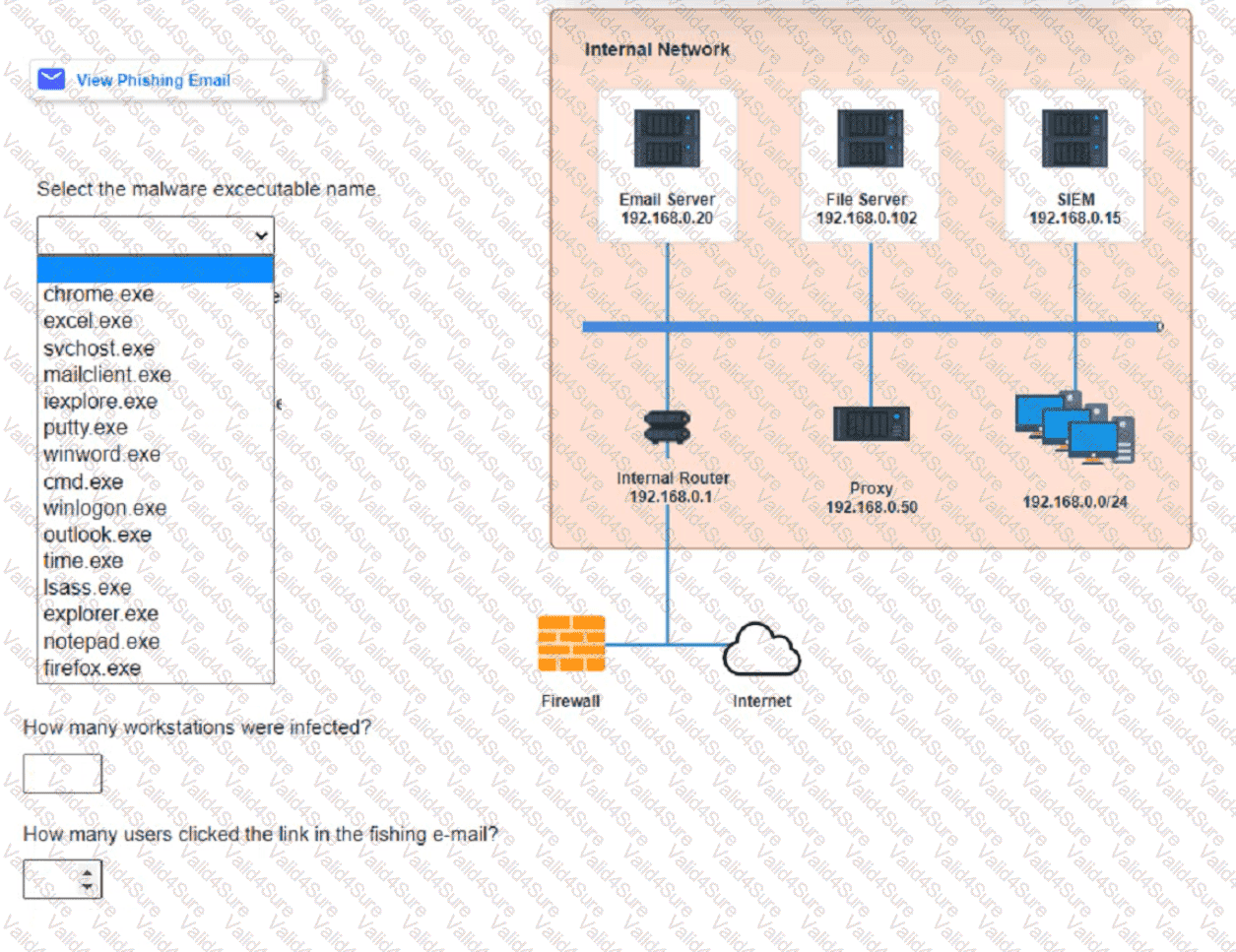
Approximately 100 employees at your company have received a Phishing email. AS a security analyst. you have been tasked with handling this Situation.


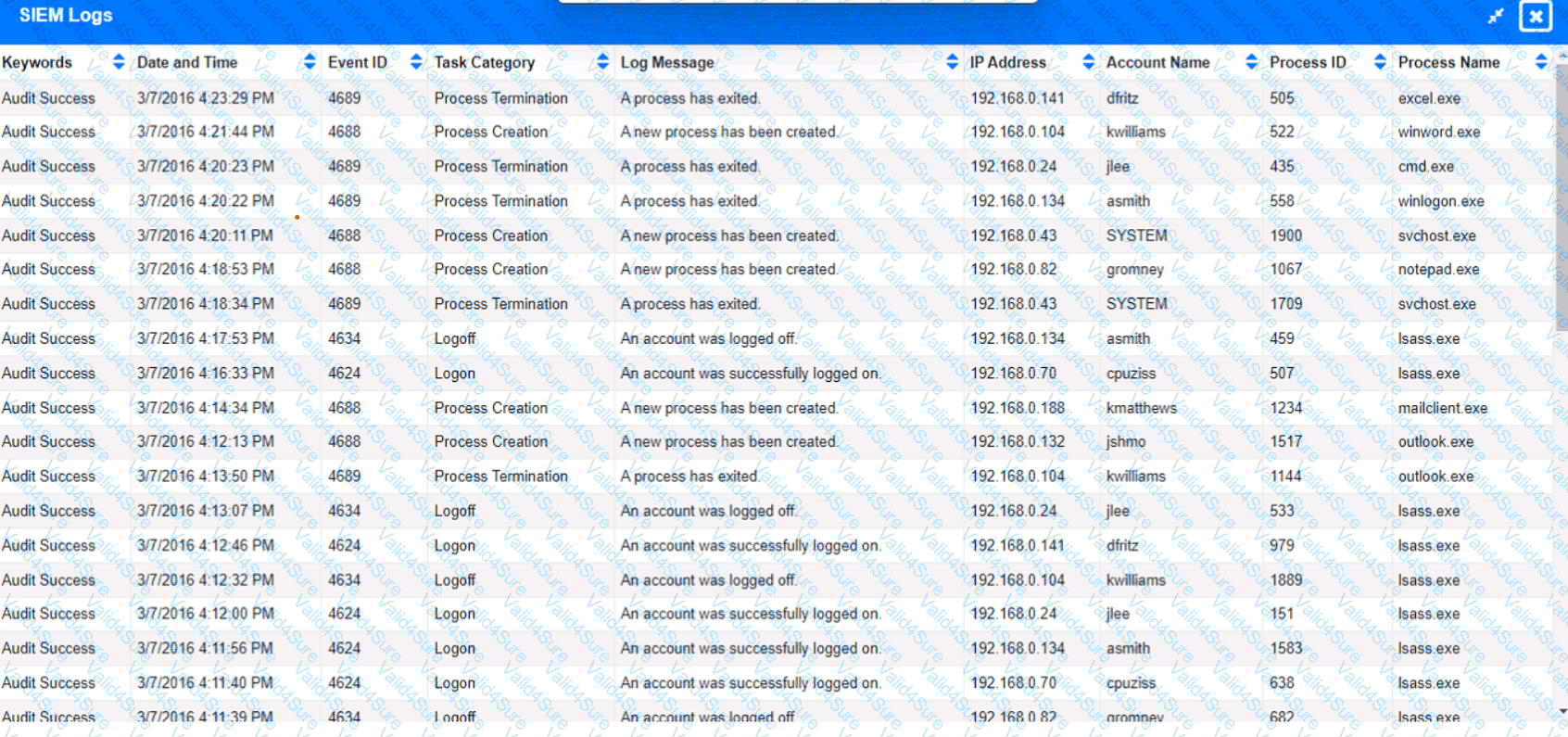
Review the information provided and determine the following:
1. HOW many employees Clicked on the link in the Phishing email?
2. on how many workstations was the malware installed?
3. what is the executable file name of the malware?
A systems administrator is reviewing after-hours traffic flows from data center servers and sees regular, outgoing HTTPS connections from one of the servers to a public IP address. The server should not be making outgoing connections after hours. Looking closer, the administrator sees this traffic pattern around the clock during work hours as well. Which of the following is the most likely explanation?