AZ-500 Exam Dumps - Microsoft Azure Security Technologies
Searching for workable clues to ace the Microsoft AZ-500 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s AZ-500 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
You are securing access to the resources in an Azure subscription.
A new company policy states that all the Azure virtual machines in the subscription must use managed disks.
You need to prevent users from creating virtual machines that use unmanaged disks.
What should you use?
You have an Azure subscription that contains an Azure Active Directory (Azure AD) tenant and a user named User1.
The App registrations settings for the tenant are configured as shown in the following exhibit.
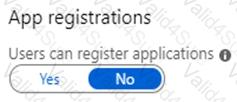
You plan to deploy an app named App1.
You need to ensure that User1 can register App1 in Azure AD. The solution must use the principle of least privilege.
Which role should you assign to User1?
You need to implement the planned change for WAF1.
The solution must minimize administrative effort
What should you do?
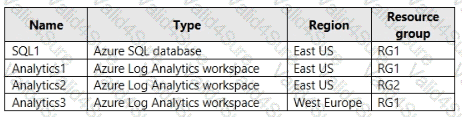
You have an Azure subscription that contains the resources shown in the following table.
You create the Azure Storage accounts shown in the following table.
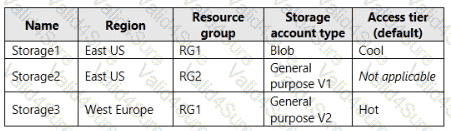
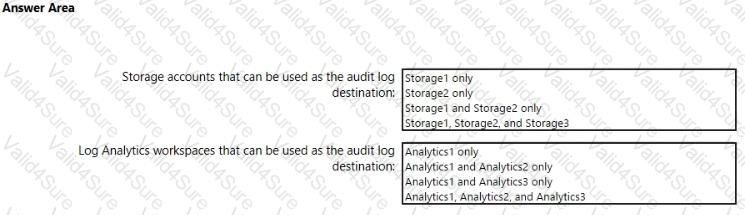
You need to configure auditing for SQL1.
Which storage accounts and Log Analytics workspaces can you use as the audit log destination? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You have an Azure subscription that contains an Azure API Management instance named ContosoAPI1.
You need to configure SSL 3.0 support for ContosoAPI1.
What should you do first in the Azure portal?
You have an Azure subscription that contains the resources shown in the following table.
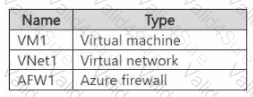
You need to configure AFW1 to only allow traffic from VM1 to storage accounts in the West US Azure region. The solution must minimize administrative effort.
What should you configure?
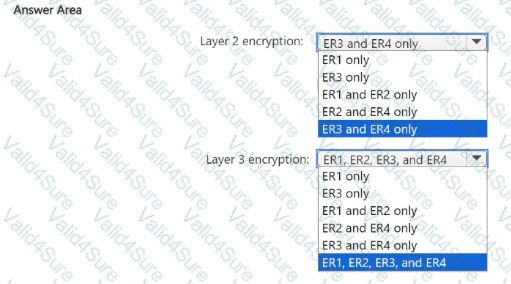
You need to recommend an encryption solution for the planned ExpressRoute implementation. The solution must meet the technical requirements.
Which ExpressRoute circuit should you recommend for each type of encryption? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You need to configure the AKS1 and ID1 managed identities to meet the technical requirements. The solution must follow the principle of least privilege.
Which role should you assign to each identity? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
