AZ-500 Exam Dumps - Microsoft Azure Security Technologies
Searching for workable clues to ace the Microsoft AZ-500 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s AZ-500 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
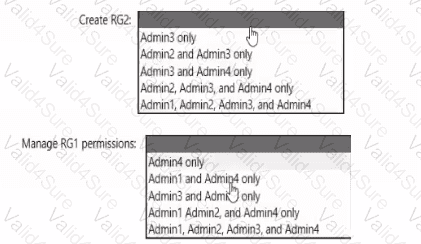
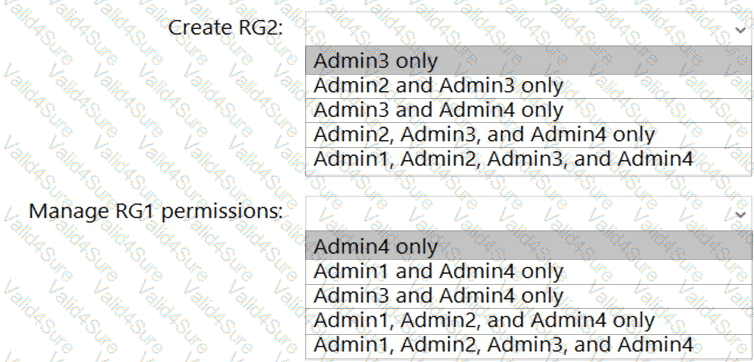
You need to delegate the creation of RG2 and the management of permissions for RG1. Which users can perform each task? To answer select the appropriate options in the answer area. NOTE: Each correct selection is worth one point
You need to meet the technical requirements for the finance department users.
Which CAPolicy1 settings should you modify?
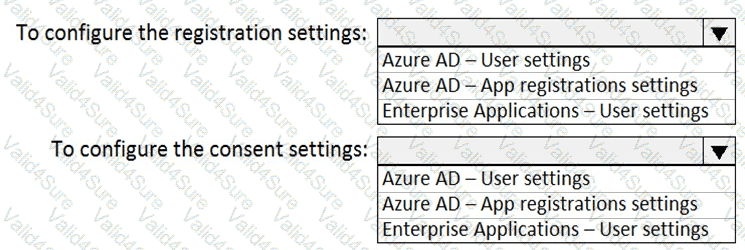
You need to ensure that the Azure AD application registration and consent configurations meet the identity and access requirements.
What should you use in the Azure portal? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You have an Azure subscription that uses Azure Active Directory (Azure AD) Privileged Identity Management (PIM).
A PIM user that is assigned the User Access Administrator role reports receiving an authorization error when performing a role assignment or viewing the list of assignments.
You need to resolve the issue by ensuring that the PIM service principal has the correct permissions for the subscription. The solution must use the principle of least privilege.
Which role should you assign to the PIM service principle?
You have an Azure subscription.
You plan to deploy a new Conditional Access policy named CAPolicy1.
You need to use the What If tool to evaluate how CAPolicy1 will affect uter1. The solution must minimize the impact of CAPolicy1 on the users.
To what should you set the Enable policy setting for CAPolicy1?
You have an Azure environment.
You need to identify any Azure configurations and workloads that are non-compliant with ISO 27001
standards. What should you use?
You plan to create an Azure Kubernetes Service (AKS) cluster in an Azure subscription.
The manifest of the registered server application is shown in the following exhibit.

You need to ensure that the AKS cluster and Azure Active Directory (Azure AD) are integrated.
Which property should you modify in the manifest?
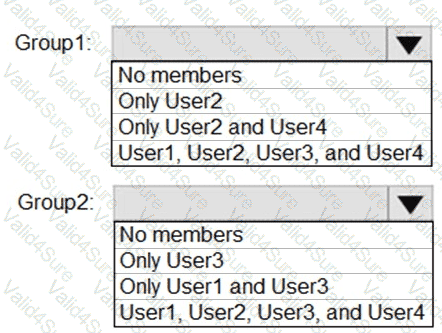
What is the membership of Group1 and Group2? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
 Graphical user interface, text, application, chat or text message Description automatically generated
Graphical user interface, text, application, chat or text message Description automatically generated