500-220 Exam Dumps - Engineering Cisco Meraki Solutions (ECMS) v2.2
Searching for workable clues to ace the Cisco 500-220 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s 500-220 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
Which VLAN is used to source pings across the site-to-site VPN when using the MX Live tools?
A Cisco Meraki MV camera is monitoring an office and its field of vision currently captures work desks and employee computer screens. However, recording employee computer screens is prohibited by local regulation.
Which feature in Dashboard can be used to preserve the current position of the camera while also meeting regulation requirements?
What is the role of the Meraki Dashboard as the service provider when using SAML for single sign-on to the Dashboard?
The WAN connection of a Cisco Meraki MX security appliance is congested, and the MX appliance is buffering the traffic from LAN ports going to the WAN ports. High, normal, and low priority queue buffers are all full. Which proportion of the normal traffic is forwarded compared to the other queues?
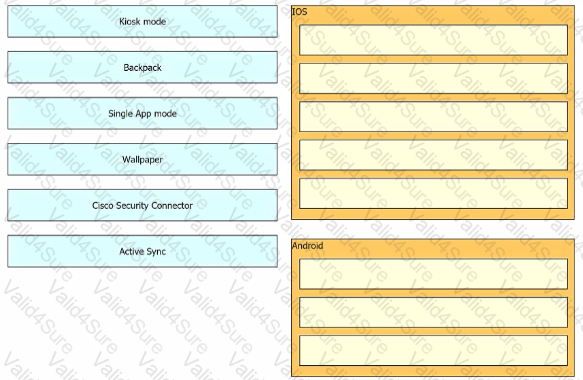
Drag and drop the settings from the left onto the OS system or systems that support it on the right Settings can be used more than once.