312-96 Exam Dumps - Certified Application Security Engineer (CASE) JAVA
Searching for workable clues to ace the ECCouncil 312-96 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s 312-96 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
Oliver is a web server admin and wants to configure the Tomcat server in such a way that it should not serve index pages in the absence of welcome files. Which of the following settings in CATALINA_HOME/conf/ in web.xml will solve his problem?
Which of the following elements in web.xml file ensures that cookies will be transmitted over an encrypted channel?
The developer wants to remove the HttpSessionobject and its values from the client' system.
Which of the following method should he use for the above purpose?
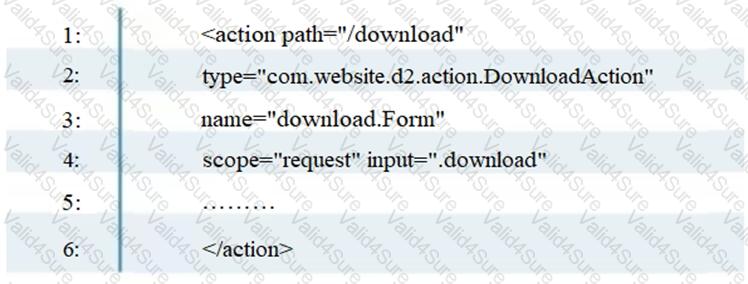
To enable the struts validator on an application, which configuration setting should be applied in the struts validator configuration file?