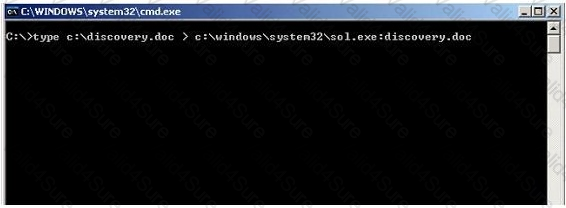
312-49v9 Exam Dumps - Computer Hacking Forensic Investigator (v9)
Searching for workable clues to ace the ECCouncil 312-49v9 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s 312-49v9 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
Which of the following tasks DOES NOT come under the investigation phase of a cybercrime forensics investigation case?
Linux operating system has two types of typical bootloaders namely LILO (Linux Loader) and GRUB (Grand Unified Bootloader). In which stage of the booting process do the bootloaders become active?
Which of the following attacks allows an attacker to access restricted directories, including application source code, configuration and critical system files, and to execute commands outside of the web server’s root directory?
Which among the following files provides email header information in the Microsoft Exchange server?
Which of the following commands shows you the names of all open shared files on a server and the number of file locks on each file?
What method of copying should always be performed first before carrying out an investigation?