300-740 Exam Dumps - Designing and Implementing Secure Cloud Access for Users and Endpoints (SCAZT)
Searching for workable clues to ace the Cisco 300-740 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s 300-740 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
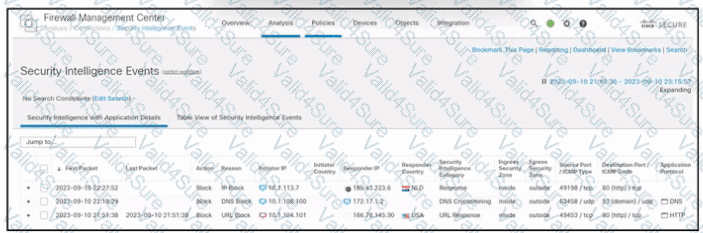
Refer to the exhibit. An engineer is analyzing a Cisco Secure Firewall Management Center report. Which activity does the output verify?
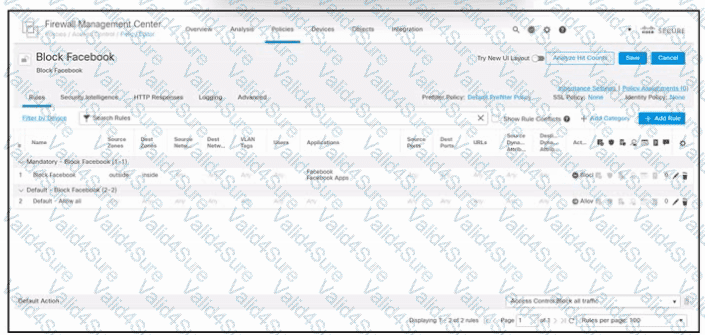
Refer to the exhibit. An engineer must block internal users from accessing Facebook and Facebook Apps. All other access must be allowed. The indicated policy was created in Cisco Secure Firewall Management Center and deployed to the internet edge firewall; however, users still can access Facebook. Which two actions must be taken to meet the requirement? (Choose two.)
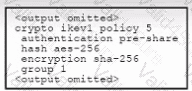
Refer to the exhibit. An engineer must configure a remote access IPsec/IKEv1 VPN that will use AES256 and SHA256 on a Cisco ASA firewall. The indicated configuration was applied to the firewall; however, the tunnel fails to establish. Which two IKEv1 policy commands must be run to meet the requirement? (Choose two.)
According to the MITRE ATT&CK framework, which approach should be used to mitigate exploitation risks?
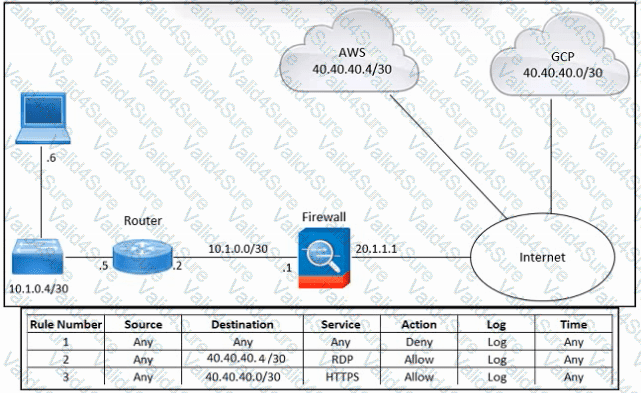
Refer to the exhibit. An engineer must provide RDP access to the AWS virtual machines and HTTPS access to the Google Cloud Platform virtual machines. All other connectivity must be blocked. The indicated rules were applied to the firewall; however, none of the virtual machines in AWS and Google Cloud Platform are accessible. What should be done to meet the requirement?