300-740 Exam Dumps - Designing and Implementing Secure Cloud Access for Users and Endpoints (SCAZT)
Searching for workable clues to ace the Cisco 300-740 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s 300-740 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
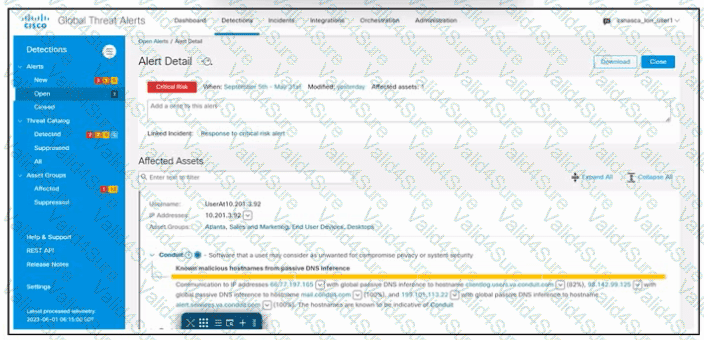
Refer to the exhibit. An engineer is investigating the critical alert received in Cisco Secure Network Analytics. The engineer confirms that the incident is valid. Which two actions must be taken? (Choose two.)
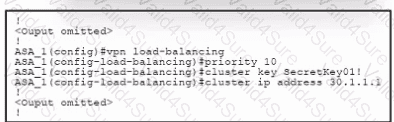
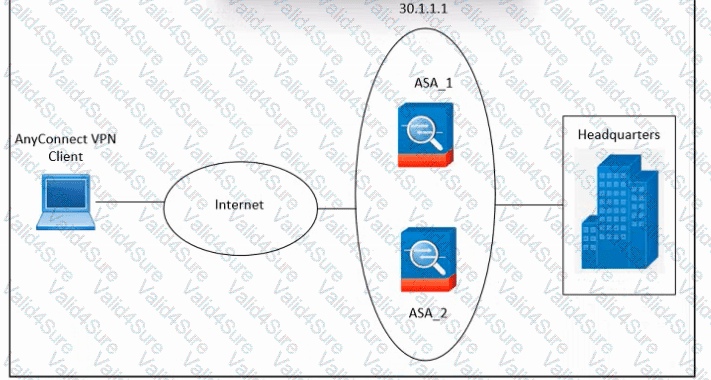
Refer to the exhibit. An engineer must configure VPN load balancing across two Cisco ASA. The indicated configuration was applied to each firewall; however, the load-balancing encryption scheme fails to work. Which two commands must be run on each firewall to meet the requirements? (Choose two.)

Refer to the exhibit. An engineer must configure SAML SSO in Cisco ISE to use Microsoft Azure AD as an identity provider. These configurations were performed:
Configure a SAML IdP in ISE.
Configure the Azure AD IdP settings.
Which two actions must the engineer take in Cisco ISE? (Choose two.)
An administrator must deploy an endpoint posture policy for all users. The organization wants to have all endpoints checked against antimalware definitions and operating system updates and ensure that the correct Secure Client modules are installed properly. How must the administrator meet the requirements?
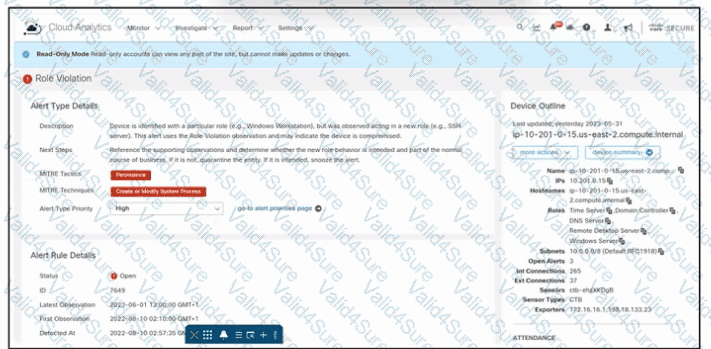

Refer to the exhibit. An engineer is troubleshooting an incident by using Cisco Secure Cloud Analytics. What is the cause of the issue?
A recent InfraGard news release indicates the need to establish a risk ranking for all on-premises and cloud services. The ACME Corporation already performs risk assessments for on-premises services and has applied a risk ranking to them. However, the cloud services that were used lack risk rankings. What Cisco Umbrella function should be used to meet the requirement?