300-415 Exam Dumps - Implementing Cisco SD-WAN Solutions (300-415 ENSDWI)
Searching for workable clues to ace the Cisco 300-415 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s 300-415 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
Which destination UDP port is used by WAN Edge router to make a DTLS connection with vBond Orchestrator?
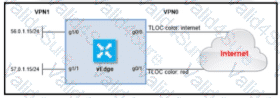
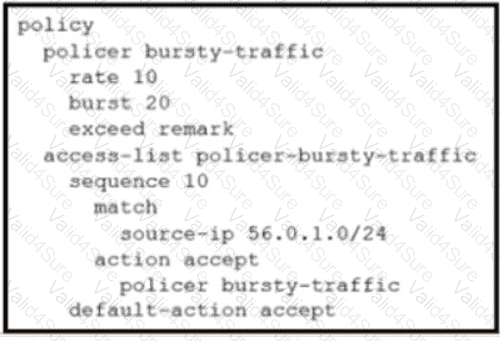
Refer to the exhibit. The ge0/0 interface connects to a 30-MB link. A network administrator wants to always have 10 MB available for high priority traffic. When lower-priority traffic busts exceed 20 MB. Traffic should be redirected to the second WAN interface ge0/1. Which set of configurations accomplishes this task?
A)
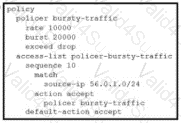
B)
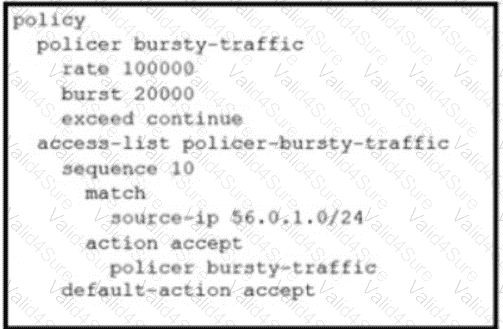
C)
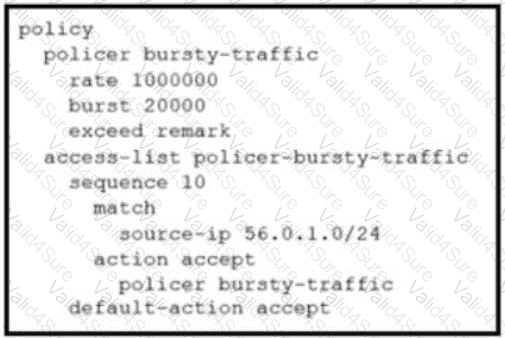
D)
When a WAN Edge device joins the SD-WAN overlay, which Cisco SD-WAN components orchestrates the connection between the WAN Edge device and a vSmart controller?
Refer to the exhibit.
An SD-WAN customer has 23 sites connected to its hub site, where a pair of WAN Edge devices and controllers are placed. All other branches have a single WAN Edge device connected to multiprotocol label switching (MPLS) and public internet circuits. An engineer must configure application-aware routing for a branch that has MPLS and public internet circuits provisioned using feature templates. The requirements for application-aware routing are:
All types of traffic prefers using public-internet circuit.
If the average latency reaches 100 ms, jitter 85 ms, and packet loss 5%, then video and voice traffic switches to the MPLS circuit.
Which feature template must be configured or modified in addition to configuring a centralized policy?
Refer to the exhibit.
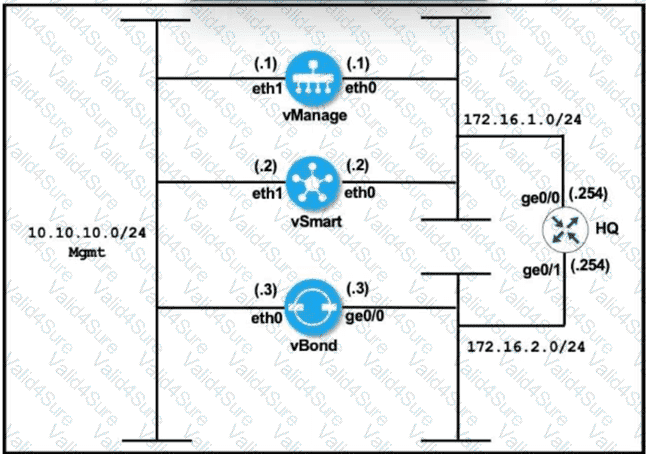
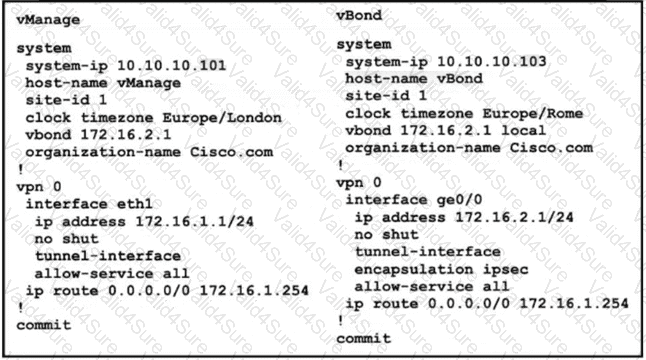
vManage and vBond have an issue establishing a connection to each other. Which configuration resolves the issue?
Which protocol is used between redundant vSmart controllers to establish a permanent communication channel?
Which two virtualized environments are available for a company to install the controllers using the on-premises model? (Choose two )
What are the default username and password for vSmart Controller when it is installed on a VMware ESXi hypervisor'?