300-220 Exam Dumps - Conducting Threat Hunting and Defending using Cisco Technologies for Cybersecurity 300-220 CBRTHD
Searching for workable clues to ace the Cisco 300-220 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s 300-220 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
A security architect is designing a threat model for a multi-tier cloud application that includes public APIs, backend microservices, and an identity provider. The goal is to identify how an attacker could chain multiple weaknesses together to achieve account takeover and data exfiltration. Which threat modeling technique is MOST appropriate?
A SOC team using Cisco security technologies wants to improve its ability to detect threats that bypass traditional security controls by abusing valid user credentials. Which hunting focus MOST effectively addresses this challenge?
A SOC analyst using Cisco security tools wants to differentiatethreat huntingfromtraditional detection engineering. Which activity BEST represents threat hunting rather than detection engineering?
A threat hunter usesCisco Secure Endpointto investigate a suspected credential-harvesting attack that does not involve dropping files to disk. Which capability is MOST critical for detecting this activity?
A security team wants to create a plan to protect companies from lateral movement attacks. The team already implemented detection alerts for pass-the-hash and pass-the-ticket techniques. Which two components must be monitored to hunt for lateral movement attacks on endpoints? (Choose two.)
Refer to the exhibit.
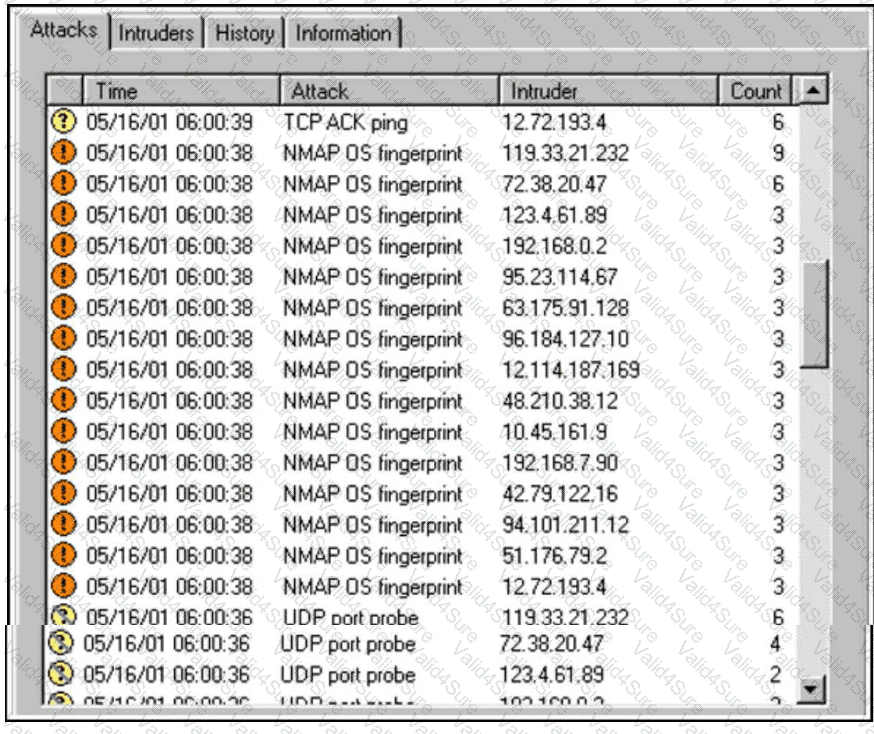
An increase in company traffic is observed by the SOC team. After they investigate the spike, it is concluded that the increase is due to ongoing scanning activity. Further analysis reveals that an adversary used Nmap for OS fingerprinting. Which type of indicators used by the adversary sits highest on the Pyramid of Pain?
According to the MITRE ATT&CK framework, how is the password spraying technique classified?
Refer to the exhibit.
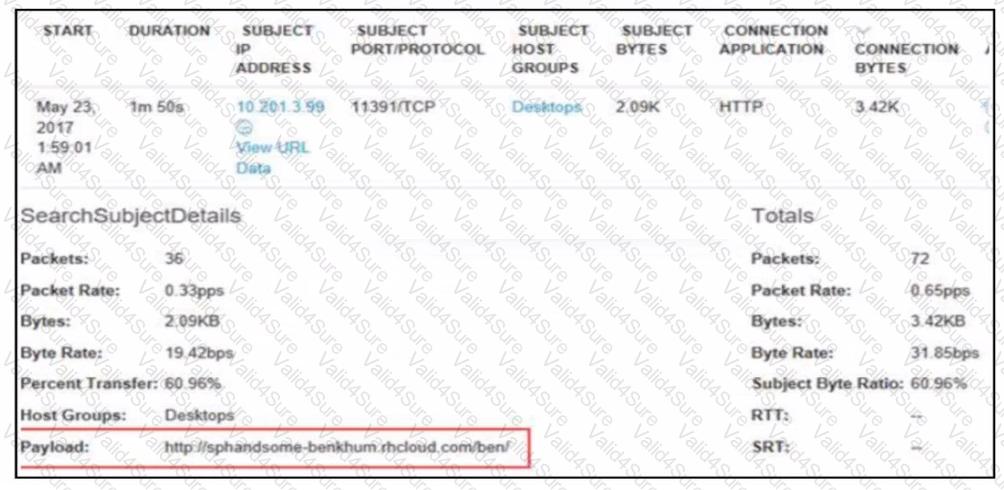
A security analyst receives an alert from Cisco Secure Network Analytics (formerly StealthWatch) with the C2 category. Which information aids the investigation?