300-215 Exam Dumps - Conducting Forensic Analysis and Incident Response Using Cisco CyberOps Technologies (CBRFIR)
Searching for workable clues to ace the Cisco 300-215 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s 300-215 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
A network host is infected with malware by an attacker who uses the host to make calls for files and shuttle traffic to bots. This attack went undetected and resulted in a significant loss. The organization wants to ensure this does not happen in the future and needs a security solution that will generate alerts when command and control communication from an infected device is detected. Which network security solution should be recommended?
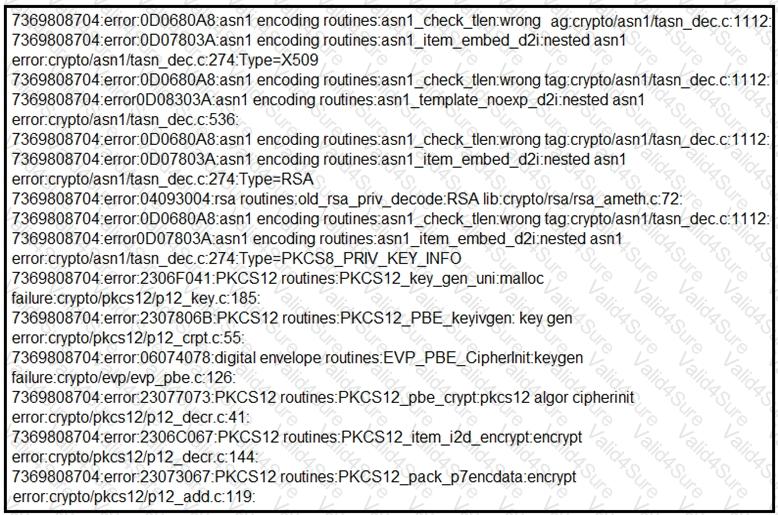
Refer to the exhibit.
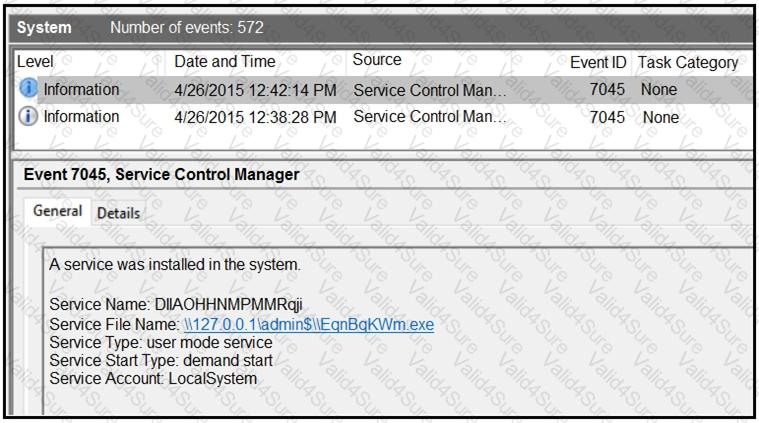
An HR department submitted a ticket to the IT helpdesk indicating slow performance on an internal share server. The helpdesk engineer checked the server with a real-time monitoring tool and did not notice anything suspicious. After checking the event logs, the engineer noticed an event that occurred 48 hours prior. Which two indicators of compromise should be determined from this information? (Choose two.)
Data has been exfiltrated and advertised for sale on the dark web. A web server shows:
Database unresponsiveness
PageFile.sys changes
Disk usage spikes with CPU spikes
High page faults
Which action should the IR team perform on the server?

Refer to the exhibit. A security analyst notices that a web application running on NGINX is generating an unusual number of log messages. The application is operational and reachable. What is the cause of this activity?