200-901 Exam Dumps - DevNet Associate (DEVASC)
Searching for workable clues to ace the Cisco 200-901 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s 200-901 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
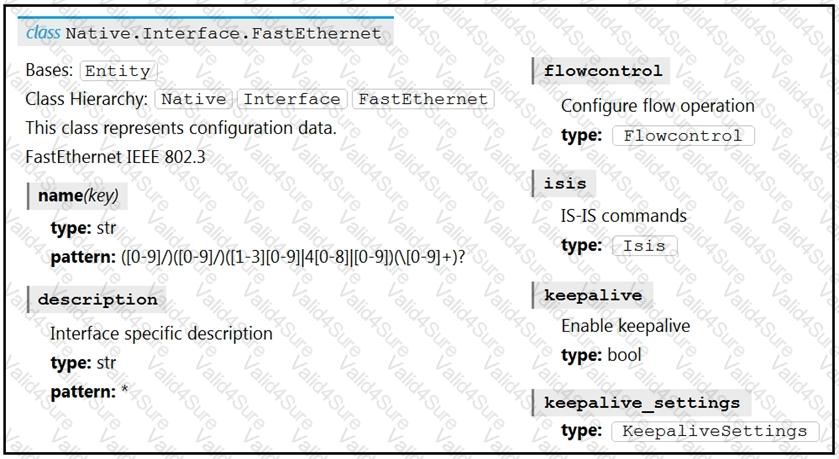
Refer to the exhibit. Drag and drop the code snippets from the bottom to the blanks in the code to enable keepalive for the FastEthernet 2/0 interface. Not all options are used.
While developing a real-Time VoIP application on a Cisco Webex platform, users report that their voice gets chopped or parts of the conversation drop out. Which network constraint is impacting the application?
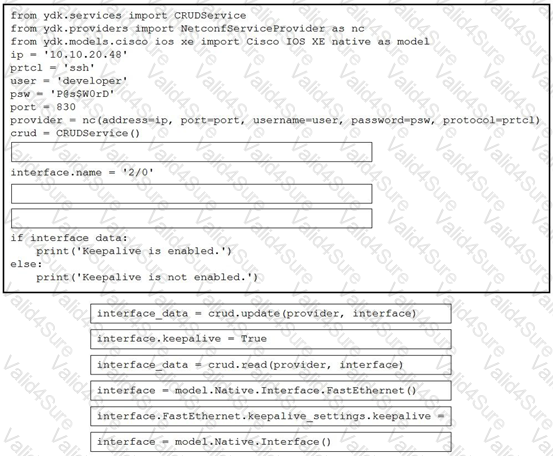
Refer to the exhibit.
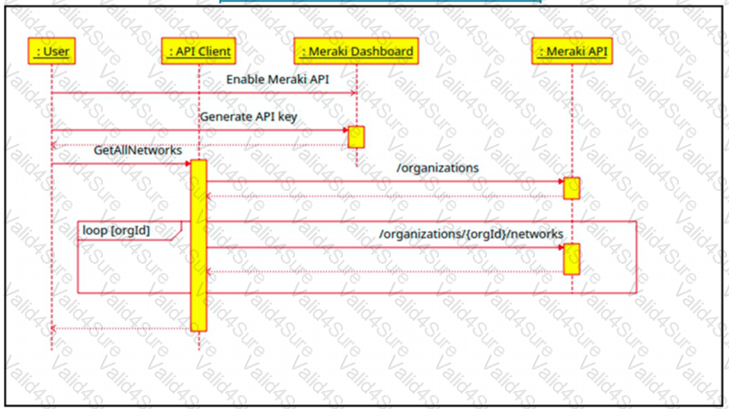
The Cisco Meraki API manages two organizations. In each organization, two independent networks are defined. How many calls to the /organizations/(orgid)networks endpoint will be run parallel by the GetAllNetwork function of the API client?