Note! Following 1z0-1104-23 Exam is Retired now. Please select the alternative replacement for your Exam Certification.
The new exam code is 1z0-1104-24
1z0-1104-23 Exam Dumps - Oracle Cloud Infrastructure 2023 Security Professional
Question # 4
Which two are monitored by Cloud Guard in OCI, which can help with the overall security posture? (Choose two.)
Question # 5
Which value must an application have to retrieve a secret bundle from Oracle Cloud Infrastructure? (Choose the best Answer.)
Question # 6
Which cache rules criterion matches if the concatenation of the requested URL path and query are identical to the contents of the value field?
Question # 8
As a security architect, how can you preventunwanted bots while desirable bots are allowed to enter?
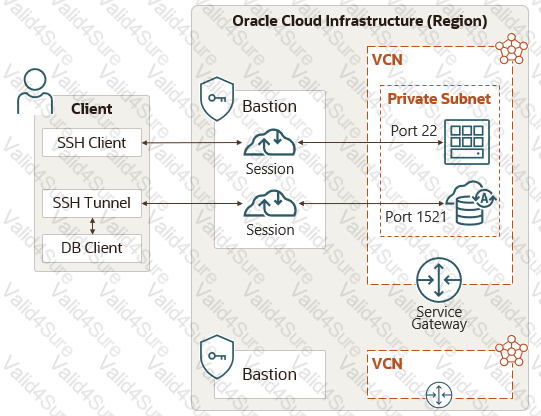 Diagram Description automatically generated
Diagram Description automatically generated