- Home
- Paloalto Networks
- Security Operations
- XDR-Engineer - Palo Alto Networks XDR Engineer
XDR-Engineer Exam Dumps - Palo Alto Networks XDR Engineer
Searching for workable clues to ace the Paloalto Networks XDR-Engineer Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s XDR-Engineer PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
What is the earliest time frame an alert could be automatically generated once the conditions of a new correlation rule are met?
Between 30 and 45 minutes
Immediately
5 minutes or less
Between 10 and 20 minutes
Answer:
Explanation:
In Cortex XDR,correlation rulesare used to detect specific patterns or behaviors by analyzing ingested data and generating alerts when conditions are met. The time frame for alert generation depends on the data ingestion pipeline, the processing latency of the Cortex XDR backend, and the rule’s evaluation frequency. For a new correlation rule, once the conditions are met (i.e., the relevant events are ingested and processed), Cortex XDR typically generates alerts within a short time frame, often5 minutes or less, due to its near-real-time processing capabilities.
Correct Answer Analysis (C):Theearliest time framefor an alert to be generated is5 minutes or less, as Cortex XDR’s architecture is designed to process and correlate events quickly. This accounts for the time to ingest data, evaluate the correlation rule, and generate the alert in the system.
Why not the other options?
A. Between 30 and 45 minutes: This time frame is too long for Cortex XDR’s near-real-time detection capabilities. Such delays might occur in systems with significant processing backlogs, but not in a properly configured Cortex XDR environment.
B. Immediately: While Cortex XDR is fast, “immediately†implies zero latency, which is not realistic due to data ingestion, processing, and rule evaluation steps. A small delay (within 5 minutes) is expected.
D. Between 10 and 20 minutes: This is also too long for the earliest possible alert generation in Cortex XDR, as the system is optimized for rapid detection and alerting.
Exact Extract or Reference:
TheCortex XDR Documentation Portalexplains correlation rule processing: “Alerts are generated within 5 minutes or less after the conditions of a correlation rule are met, assuming data is ingested and processed in near real-time†(paraphrased from the Correlation Rules section). TheEDU-262: Cortex XDR Investigation and Responsecourse covers detection engineering, stating that “Cortex XDR’s correlation engine processes rules and generates alerts typically within a few minutes of event ingestion†(paraphrased from course materials). ThePalo Alto Networks Certified XDR Engineer datasheetincludes “detection engineering†as a key exam topic, encompassing correlation rule alert generation.
Based on the SBAC scenario image below, when the tenant is switched to permissive mode, which endpoint(s) data will be accessible?
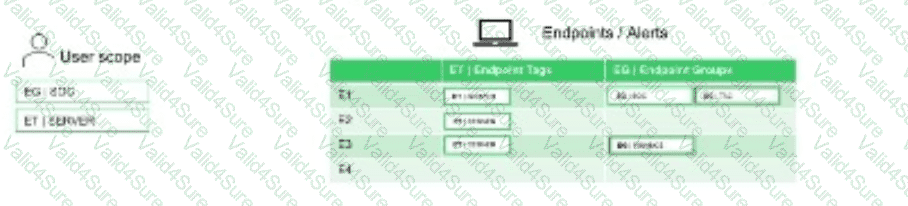
E1 only
E2 only
E1, E2, and E3
E1, E2, E3, and E4
Answer:
Explanation:
In Cortex XDR,Scope-Based Access Control (SBAC)restricts user access to data based on predefined scopes, which can be assigned to endpoints, users, or other resources. Inpermissive mode, SBAC allows users to access data within their assigned scopes but may restrict access to data outside those scopes. The question assumes an SBAC scenario with four endpoints (E1, E2, E3, E4), where the user likely has access to a specific scope (e.g., Scope A) that includes E1, E2, and E3, while E4 is in a different scope (e.g., Scope B).
Correct Answer Analysis (C):When the tenant is switched to permissive mode, the user will have access toE1, E2, and E3because these endpoints are within the user’s assigned scope (e.g., Scope A). E4, being in a different scope (e.g., Scope B), will not be accessible unless the user has explicit accessto that scope. Permissive mode enforces scope restrictions, ensuring that only data within the user’s scope is visible.
Why not the other options?
A. E1 only: This is too restrictive; the user’s scope includes E1, E2, and E3, not just E1.
B. E2 only: Similarly, this is too restrictive; the user’s scope includes E1, E2, and E3, not just E2.
D. E1, E2, E3, and E4: This would only be correct if the user had access to both Scope A and Scope B or if permissive mode ignored scope restrictions entirely, which it does not. Permissive mode still enforces SBAC rules, limiting access to the user’s assigned scopes.
Exact Extract or Reference:
TheCortex XDR Documentation Portalexplains SBAC: “In permissive mode, Scope-Based Access Control restricts user access to endpoints within their assigned scopes, ensuring data visibility aligns with scope permissions†(paraphrased from the Scope-Based Access Control section). TheEDU-260: Cortex XDR Prevention and Deploymentcourse covers SBAC configuration, stating that “permissive mode allows access to endpoints within a user’s scope, such as E1, E2, and E3, while restricting access to endpoints in other scopes†(paraphrased from course materials). ThePalo Alto Networks Certified XDR Engineer datasheetincludes “post-deployment management and configuration†as a key exam topic, encompassing SBAC settings.
Using the Cortex XDR console, how can additional network access be allowed from a set of IP addresses to an isolated endpoint?
Add entries in Configuration section of Security Settings
Add entries in the Allowed Domains section of Security Settings for the tenant
Add entries in Exceptions Configuration section of Isolation Exceptions
Add entries in Response Actions section of Agent Settings profile
Answer:
Explanation:
In Cortex XDR,endpoint isolationis a response action that restricts network communication to and from an endpoint, allowing only communication with the Cortex XDR management server to maintain agent functionality. To allow additional network access (e.g., from a set of IP addresses) to an isolated endpoint, administrators can configureisolation exceptionsto permit specific traffic while the endpoint remains isolated.
Correct Answer Analysis (C):TheExceptions Configuration section of Isolation Exceptionsin the Cortex XDR console allows administrators to define exceptions for isolated endpoints, such as permitting network access from specific IP addresses. This ensures that the isolated endpoint can communicate with designated IPs (e.g., for IT support or backup servers) while maintaining isolation from other network traffic.
Why not the other options?
A. Add entries in Configuration section of Security Settings: The Security Settings section in the Cortex XDR console is used for general tenant-wide configurations (e.g., password policies), not for managing isolation exceptions.
B. Add entries in the Allowed Domains section of Security Settings for the tenant: The Allowed Domains section is used to whitelist domains for specific purposes (e.g., agent communication), not for defining IP-based exceptions for isolated endpoints.
D. Add entries in Response Actions section of Agent Settings profile: The Response Actions section in Agent Settings defines automated response actions (e.g., isolate on specific conditions), but it does not configure exceptions for already isolated endpoints.
Exact Extract or Reference:
TheCortex XDR Documentation Portalexplains isolation exceptions: “To allow specific network access to an isolated endpoint, add IP addresses or domains in the Exceptions Configuration section of Isolation Exceptions in the Cortex XDR console†(paraphrased from the Endpoint Isolation section). TheEDU-262: Cortex XDR Investigation and Responsecourse covers isolation management, stating that “Isolation Exceptions allow administrators to permit network access from specific IPs to isolated endpoints†(paraphrased from course materials). ThePalo Alto Networks Certified XDR Engineer datasheetincludes “post-deployment management and configuration†as a key exam topic, encompassing isolation exception configuration.
How long is data kept in the temporary hot storage cache after being queried from cold storage?
1 hour, re-queried to a maximum of 12 hours
24 hours, re-queried to a maximum of 7 days
24 hours, re-queried to a maximum of 14 days
1 hour, re-queried to a maximum of 24 hours
Answer:
Explanation:
In Cortex XDR, data is stored in different tiers:hot storage(for recent, frequently accessed data),cold storage(for older, less frequently accessed data), and atemporary hot storage cachefor data retrieved from cold storage during queries. When data is queried from cold storage, it is moved to the temporary hot storage cache to enable faster access for subsequent queries. The question asks how long this data remains in the cache and the maximum duration for re-queries.
Correct Answer Analysis (B):Data retrieved from cold storage is kept in the temporary hot storage cache for24 hours. If the data is re-queried within this period, it remains accessible in the cache. The maximum duration for re-queries is7 days, after which the data may need to be retrieved from cold storage again, incurring additional processing time.
Why not the other options?
A. 1 hour, re-queried to a maximum of 12 hours: These durations are too short and do not align with Cortex XDR’s data retention policies for the hot storage cache.
C. 24 hours, re-queried to a maximum of 14 days: While the initial 24-hour cache duration is correct, the 14-day maximum for re-queries is too long and not supported by Cortex XDR’s documentation.
D. 1 hour, re-queried to a maximum of 24 hours: The 1-hour initial cache duration is incorrect, as Cortex XDR retains queried data for 24 hours.
Exact Extract or Reference:
TheCortex XDR Documentation Portalexplains data storage: “Data queried from cold storage is cached in hot storage for 24 hours, with a maximum re-query period of 7 days†(paraphrased from the Data Management section). TheEDU-262: Cortex XDR Investigation and Responsecourse covers data retention, stating that “queried cold storage data remains in the hot cache for 24 hours, accessible for up to 7 days with re-queries†(paraphrased from course materials). ThePalo Alto Networks Certified XDR Engineer datasheetincludes “maintenance and troubleshooting†as a key exam topic, encompassing data storage management.
An analyst considers an alert with the category of lateral movement to be allowed and not needing to be checked in the future. Based on the image below, which action can an engineer take to address the requirement?

Create a behavioral indicator of compromise (BIOC) suppression rule for the parent process and the specific BIOC: Lateral movement
Create an alert exclusion rule by using the alert source and alert name
Create a disable injection and prevention rule for the parent process indicated in the alert
Create an exception rule for the parent process and the exact command indicated in the alert
Answer:
Explanation:
In Cortex XDR, alateral movementalert (mapped to MITRE ATT&CK T1021, e.g., Remote Services) indicates potential unauthorized network activity, often involving processes like cmd.exe. If the analyst determines this behavior is allowed (e.g., a legitimate use of cmd /c dir for administrative purposes) and should not be flagged in the future, the engineer needs to suppress future alerts for this specific behavior. The most effective way to achieve this is by creating analert exclusion rule, which suppresses alerts based on specific criteria such as the alert source (e.g., Cortex XDR analytics) and alert name (e.g., "Lateral Movement Detected").
Correct Answer Analysis (B):Create an alert exclusion rule by using the alert source and alert nameis the recommended action. This approach directly addresses the requirement by suppressing future alerts of the same type (lateral movement) from the specified source, ensuring that this legitimate activity (e.g., cmd /c dir by cmd.exe) does not generate alerts. Alert exclusions can be fine-tuned to apply to specific endpoints, users, or other attributes, making this a targeted solution.
Why not the other options?
A. Create a behavioral indicator of compromise (BIOC) suppression rule for the parent process and the specific BIOC: Lateral movement: While BIOC suppression rules can suppress specific BIOCs, the alert in question appears to be generated by Cortex XDR analytics (not a custom BIOC), as indicated by the MITRE ATT&CK mapping and alert category. BIOC suppression is more relevant for custom BIOC rules, not analytics-driven alerts.
C. Create a disable injection and prevention rule for the parent process indicated in the alert: There is no “disable injection and prevention rule†in CortexXDR, and this option does not align with the goal of suppressing alerts. Injection prevention is related to exploit protection, not lateral movement alerts.
D. Create an exception rule for the parent process and the exact command indicated in the alert: While creating an exception for the parent process (cmd.exe) and command (cmd /c dir) might prevent some detections, it is not the most direct method for suppressing analytics-driven lateral movement alerts. Exceptions are typically used for exploit or malware profiles, not for analytics-based alerts.
Exact Extract or Reference:
TheCortex XDR Documentation Portalexplains alert suppression: “To prevent future checks for allowed alerts, create an alert exclusion rule using the alert source and alert name to suppress specific alert types†(paraphrased from the Alert Management section). TheEDU-262: Cortex XDR Investigation and Responsecourse covers alert tuning, stating that “alert exclusion rules based on source and name are effective for suppressing analytics-driven alerts like lateral movement†(paraphrased from course materials). ThePalo Alto Networks Certified XDR Engineer datasheetincludes “detection engineering†as a key exam topic, encompassing alert suppression techniques.
A correlation rule is created to detect potential insider threats by correlating user login events from one dataset with file access events from another dataset. The rule must retain all user login events, even if there are no matching file access events, to ensure no login activity is missed.
text
Copy
dataset = x
| join (dataset = y)
Which type of join is required to maintain all records from dataset x, even if there are no matching events from dataset y?
Inner
Left
Right
Outer
Answer:
Explanation:
In Cortex XDR, correlation rules useXQL (XDR Query Language)to combine data from multiple datasets to detect patterns, such as insider threats. Thejoinoperation in XQL is used to correlate events from two datasets based on a common field (e.g., user ID). The type of join determines how records are matched and retained when there are no corresponding events in one of the datasets.
The question specifies that the correlation rule must retainall user login eventsfrom dataset x (the primary dataset containing login events), even if there are no matching file access events in dataset y (the secondary dataset). This requirement aligns with aLeft Join(also called Left Outer Join), which includes all records from the left dataset (dataset x) and any matching records from the right dataset (dataset y). If there is no match in dataset y, the result includes null values for dataset y’s fields, ensuring no login events are excluded.
Correct Answer Analysis (B):ALeft Joinensures that all records from dataset x (user login events) are retained, regardless of whether there are matching file access events in dataset y. This meets the requirement to ensure no login activity is missed.
Why not the other options?
A. Inner: An Inner Join only includes records where there is a match in both datasets (x and y). This would exclude login events from dataset x that have no corresponding file access events in dataset y, which violates the requirement.
C. Right: A Right Join includes all records from dataset y (file access events) and only matching records from dataset x. This would prioritize file access events, potentially excluding login events with no matches, which is not desired.
D. Outer: A Full Outer Join includes all records from both datasets, with nulls in places where there is no match. While this retains all login events, it also includes unmatched file access events from dataset y, which is unnecessary for the stated requirement of focusing on login events.
Exact Extract or Reference:
TheCortex XDR Documentation Portalin theXQL Reference Guideexplains join operations: “A Left Join returns all records from the left dataset and matching records from the right dataset. If there is no match, null values are returned for the right dataset’s fields†(paraphrased from the XQL Join section). TheEDU-262: Cortex XDR Investigation and Responsecourse covers correlation rules and XQL, noting that “Left Joins are used in correlation rules to ensure all events from the primary dataset are retained, even without matches in the secondary dataset†(paraphrased from course materials). ThePalo Alto Networks Certified XDR Engineer datasheetlists “detection engineering†as a key exam topic, including creating correlation rules with XQL.
What will enable a custom prevention rule to block specific behavior?
A correlation rule added to an Agent Blocking profile
A custom behavioral indicator of compromise (BIOC) added to an Exploit profile
A custom behavioral indicator of compromise (BIOC) added to a Restriction profile
A correlation rule added to a Malware profile
Answer:
Explanation:
In Cortex XDR,custom prevention rulesare used to block specific behaviors or activities on endpoints by leveragingBehavioral Indicators of Compromise (BIOCs). BIOCs define patterns of behavior (e.g., specific process executions, file modifications, or network activities) that, when detected, can trigger preventive actions, such as blocking a process or isolating an endpoint. These BIOCs are typically associated with aRestriction profile, which enforces blocking actions for matched behaviors.
Correct Answer Analysis (C):Acustom behavioral indicator of compromise (BIOC)added to aRestriction profileenables a custom prevention rule to block specific behavior. The BIOC defines the behavior to detect (e.g., a process accessing a sensitive file), and the Restriction profile specifies the preventive action (e.g., block the process). This configuration ensures that the identified behavior is blocked on endpoints where the profile is applied.
Why not the other options?
A. A correlation rule added to an Agent Blocking profile: Correlation rules are used to generate alerts by correlating events across datasets, not to block behaviors directly. There is no “Agent Blocking profile†in Cortex XDR; this is a misnomer.
B. A custom behavioral indicator of compromise (BIOC) added to an Exploit profile: Exploit profiles are used to detect and prevent exploit-based attacks (e.g., memory corruption), not general behavioral patterns defined by BIOCs. BIOCs are associated with Restriction profiles for blocking behaviors.
D. A correlation rule added to a Malware profile: Correlation rules do not directly block behaviors; they generate alerts. Malware profiles focus on file-based threats (e.g., executables analyzed by WildFire), not behavioral blocking via BIOCs.
Exact Extract or Reference:
TheCortex XDR Documentation Portalexplains BIOC and Restriction profiles: “Custom BIOCs can be added to Restriction profiles to block specific behaviors on endpoints, enabling tailored prevention rules†(paraphrased from the BIOC and Restriction Profile sections). TheEDU-260: Cortex XDR Prevention and Deploymentcourse covers prevention rules, stating that “BIOCs in Restriction profiles enable blocking of specific endpoint behaviors†(paraphrased from course materials). ThePalo Alto Networks Certified XDR Engineer datasheetincludes “detection engineering†as a key exam topic, encompassing BIOC and prevention rule configuration.