SECRET-SEN Exam Dumps - CyberArk Sentry Secrets Manager
Searching for workable clues to ace the CyberArk SECRET-SEN Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s SECRET-SEN PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
When attempting to retrieve a credential managed by the Synchronizer, you receive this error:
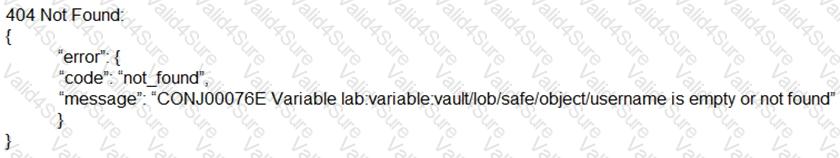
What is the cause of the issue?
After manually failing over to your disaster recovery site (Site B) for testing purposes, you need to failback to your primary site (Site A).
Which step is required?
A customer requires high availability in its AWS cloud infrastructure.
What is the minimally viable Conjur deployment architecture to achieve this?
An application owner reports that their application is suddenly receiving an incorrect password. CPM logs show the password was recently changed, but the value currently being retrieved by the application is a different value. The Vault Conjur Synchronizer service is running.
What is the most likely cause of this issue?
You are deploying Kubernetes resources/objects as Conjur identities.
In addition to Namespace and Deployment, from which options can you choose? (Choose two.)