SC-100 Exam Dumps - Microsoft Cybersecurity Architect
Searching for workable clues to ace the Microsoft SC-100 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s SC-100 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
What should you create in Azure AD to meet the Contoso developer requirements?
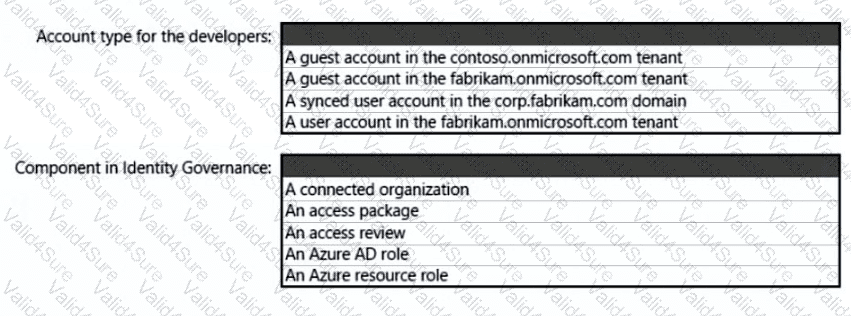
You are designing a security operations strategy based on the Zero Trust framework.
You need to minimize the operational load on Tier 1 Microsoft Security Operations Center (SOC) analysts.
What should you do?
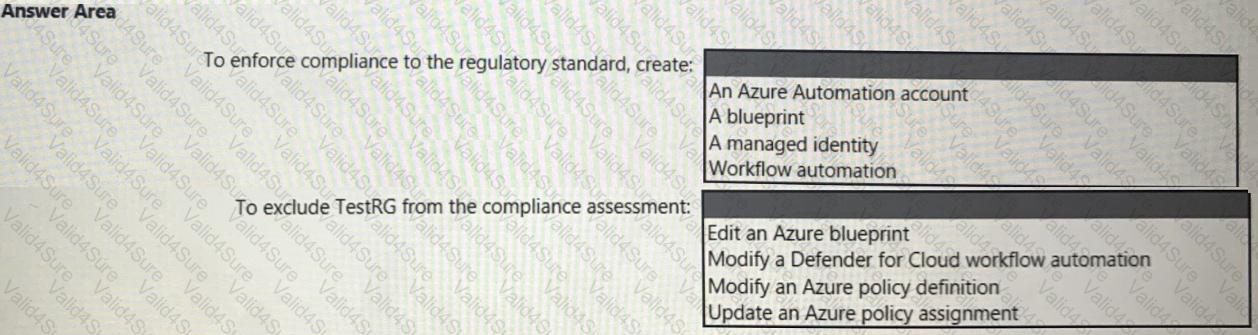
You need to recommend a solution to meet the compliance requirements.
What should you recommend? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
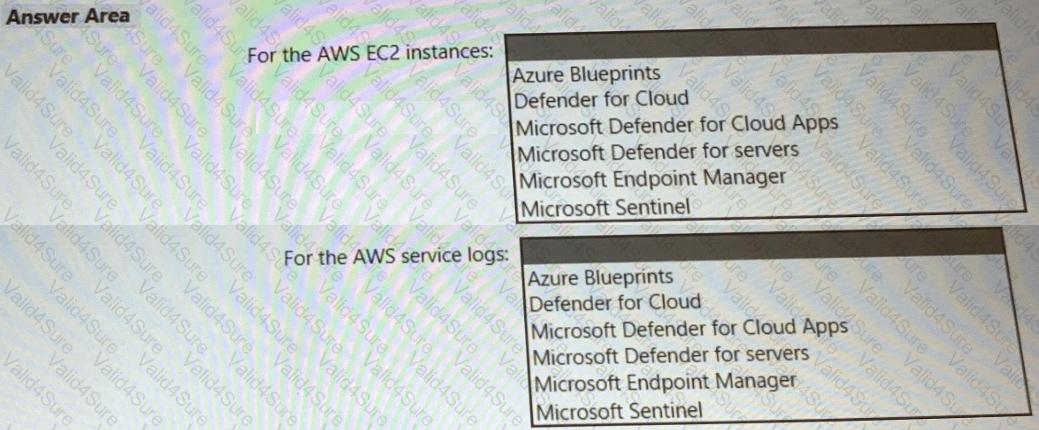
You need to recommend a solution to meet the AWS requirements.
What should you include in the recommendation? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You need to recommend a solution to meet the security requirements for the virtual machines.
What should you include in the recommendation?