PT0-003 Exam Dumps - CompTIA PenTest+ Exam
Searching for workable clues to ace the CompTIA PT0-003 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s PT0-003 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
A penetration tester finds that an application responds with the contents of the /etc/passwd file when the following payload is sent:
<!DOCTYPE data [ ]>
Which of the following should the tester recommend in the report to best prevent this type of vulnerability?
A penetration tester performs an assessment on the target company's Kubernetes cluster using kube-hunter. Which of the following types of vulnerabilities could be detected with the tool?
During an engagement, a penetration tester wants to enumerate users from Linux systems by using finger and rwho commands. However, the tester realizes these commands alone will not achieve the desired result. Which of the following is the best tool to use for this task?
A company hires a penetration tester to perform an external attack surface review as part of a security engagement. The company informs the tester that the main company domain to investigate is comptia.org. Which of the following should the tester do to accomplish the assessment objective?
While conducting a reconnaissance activity, a penetration tester extracts the following information:
Emails: - admin@acme.com - sales@acme.com - support@acme.com
Which of the following risks should the tester use to leverage an attack as the next step in the security assessment?
A tester completed a report for a new client. Prior to sharing the report with the client, which of the following should the tester request to complete a review?
Which of the following are valid reasons for including base, temporal, and environmental CVSS metrics in the findings section of a penetration testing report? (Select two).
During an engagement, a penetration tester receives a list of target systems and wants to enumerate them for possible vulnerabilities. The tester finds the following script on the internet:

After running the script, the tester runs the following command:
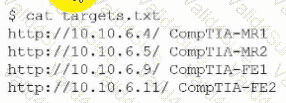
Which of the following should the tester do next?