PSE-Cortex Exam Dumps - Palo Alto Networks System Engineer - Cortex Professional
Searching for workable clues to ace the Paloalto Networks PSE-Cortex Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s PSE-Cortex PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
Which two types of indicators of compromise (IOCs) are available for creation in Cortex XDR? (Choose two.)
Which Cortex XDR capability prevents running malicious files from USB-connected removable equipment?
What method does the Traps agent use to identify malware during a scheduled scan?
A Cortex XSOAR customer wants to send a survey to users asking them to input their manager's email for a training use case so the manager can receive status reports on the employee's training. However, the customer is concerned users will provide incorrect information to avoid sending status updates to their manager.
How can Cortex XSOAR most efficiently sanitize user input prior to using the responses in the playbook?
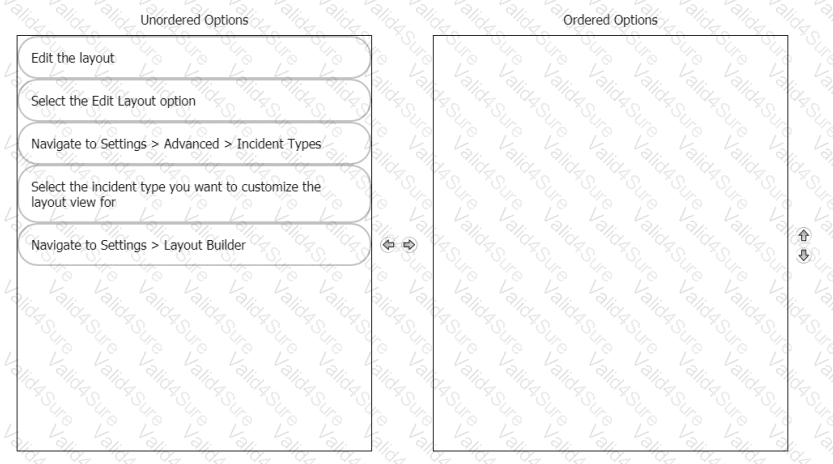
Rearrange the steps into the correct order for modifying an incident layout.
 Correct
Correct