PCNSE Exam Dumps - Palo Alto Networks Certified Security Engineer (PCNSE) PAN-OS 11.0
Searching for workable clues to ace the Paloalto Networks PCNSE Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s PCNSE PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
Review the screenshots.
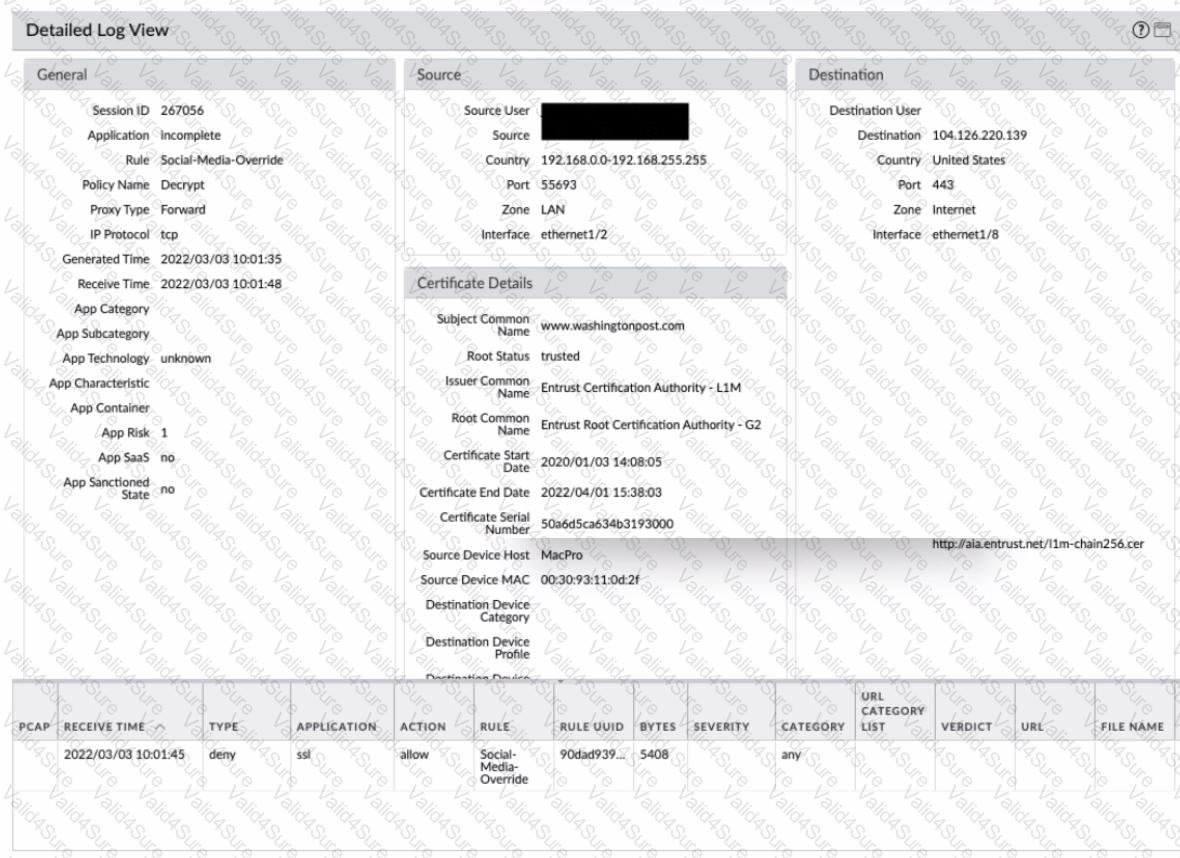
What is the most likely reason for this decryption error log?
All firewall at a company are currently forwarding logs to Palo Alto Networks log collectors. The company also wants to deploy a sylog server and forward all firewall logs to the syslog server and to the log collectors. There is known logging peak time during the day, and the security team has asked the firewall engineer to determined how many logs per second the current Palo Alto Networking log processing at that particular time. Which method is the most time-efficient to complete this task?
A firewall engineer is configuring quality of service (OoS) policy for the IP address of a specific server in an effort to limit the bandwidth consumed by frequent downloads of large files from the internet.
Which combination of pre-NAT and / or post-NAT information should be used in the QoS rule?
In the New App Viewer under Policy Optimizer, what does the compare option for a specific rule allow an administrator to compare?
An administrator has a Palo Alto Networks NGFW. All security subscriptions and decryption are enabled and the system is running close to its resource limits.
Knowing that using decryption can be resource-intensive, how can the administrator reduce the load on the firewall?
Which three multi-factor authentication methods can be used to authenticate access to the firewall? (Choose three.)