PCNSC Exam Dumps - Palo Alto Networks Certified Network Security Consultant
Searching for workable clues to ace the Paloalto Networks PCNSC Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s PCNSC PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
A speed/duplex negotiation mismatch is between the Palo Alto Networks management port and the switch it connect.
How would an administrator configure the interface to IGbps?
An administrator deploys PA-500 NGFWs as an active/passive high availability pair . Thedevices are not participating in dynamic router and preemption is disabled.
What must be verified to upgrade the firewalls to the most recent version of PAN OS® software?
Which two action would be part of an automatic solution that would block sites with untrusted certificates without enabling SSLforward proxy? (Choose two.)
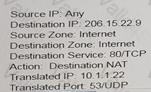
An administrator wants multiple web servers in the DMZ to receive connections from the internet. Traffic destined for 206.15.22.9 port 80/TCP needs to be forwarded to the server at 10 1.22
Based on the information shown in the age, which NAT rule will forward web-browsing traffic correctly?
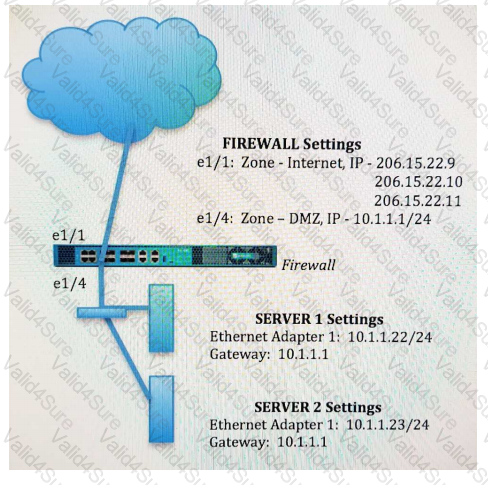
A)
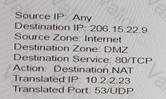
B)
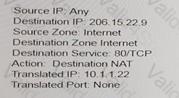
C)
D)
Which PAN-OS® policy must you configure to force a user to provide additional credential before he is allowed to access an internal application that contains highly sensitive business data?