NSE8_812 Exam Dumps - Network Security Expert 8 Written Exam
Searching for workable clues to ace the Fortinet NSE8_812 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s NSE8_812 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
SD-WAN is configured on a FortiGate. You notice that when one of the internet links has high latency the time to resolve names using DNS from FortiGate is very high.
You must ensure that the FortiGate DNS resolution times are as low as possible with the least amount of work.
What should you configure?
A retail customer with a FortiADC HA cluster load balancing five webservers in L7 Full NAT mode is receiving reports of users not able to access their website during a sale event. But for clients that were able to connect, the website works fine.
CPU usage on the FortiADC and the web servers is low, application and database servers are still able to handle more traffic, and the bandwidth utilization is under 30%.
Which two options can resolve this situation? (Choose two.)
Refer to the exhibit showing the history logs from a FortiMail device.
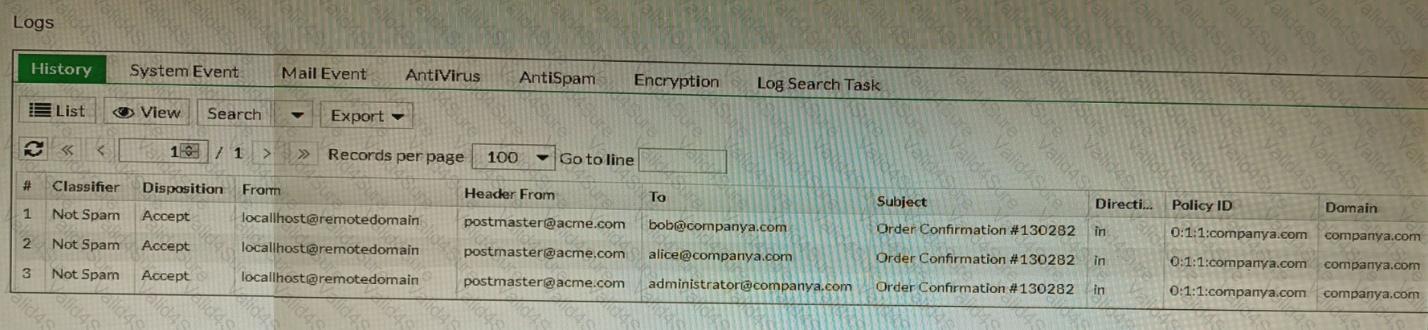
Which FortiMail email security feature can an administrator enable to treat these emails as spam?
Refer to the exhibits.
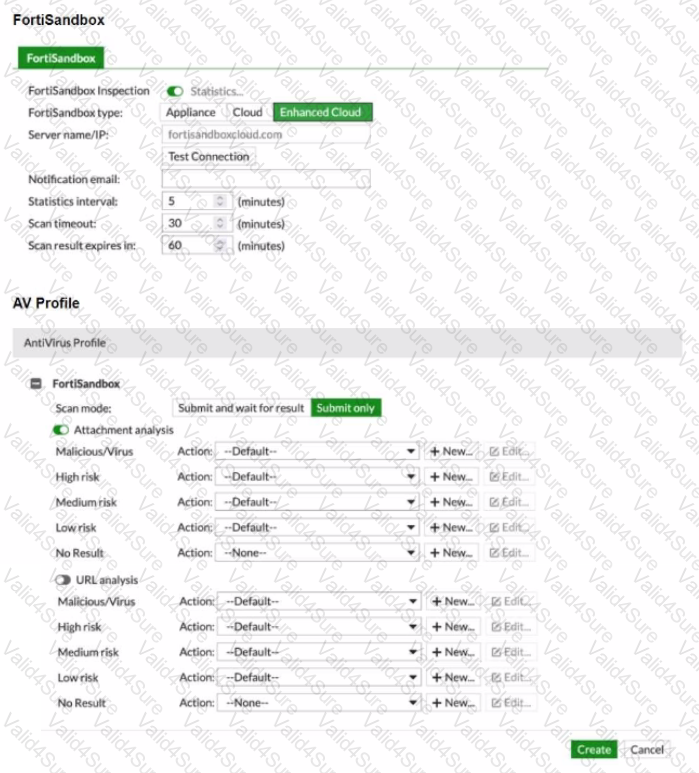
You must integrate a FortiMail and FortiSandbox Enhanced Cloud solution for a customer who is concerned about the e-mails being delayed for too long.
According to the configuration shown in the exhibits, which would be an expected behavior?
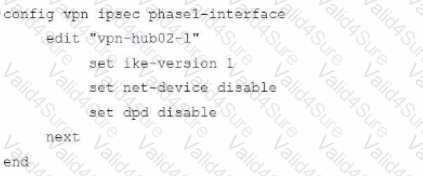
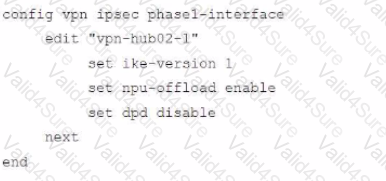
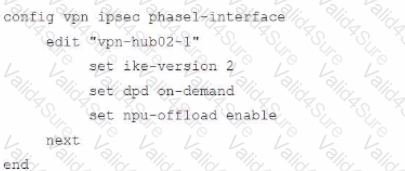
Refer to the exhibits.
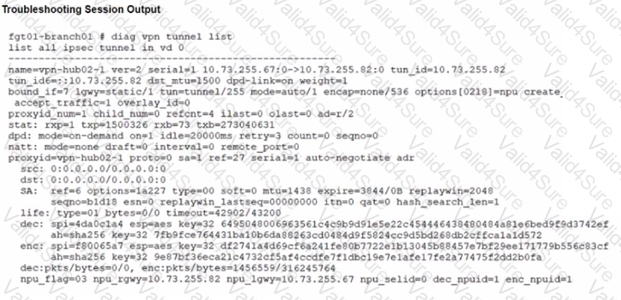
A customer is trying to restore a VPN connection configured on a FortiGate. Exhibits show output during a troubleshooting session when the VPN was working and the current baseline VPN configuration.

Which configuration parameters will restore VPN connectivity based on the diagnostic output?
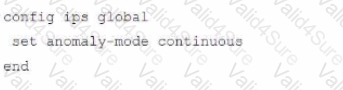
Review the Application Control log.
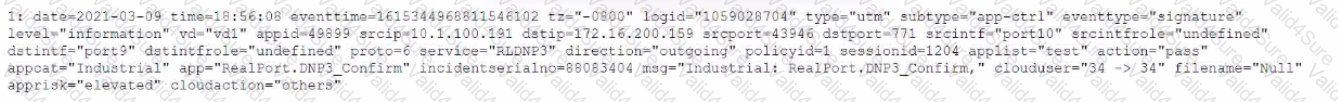
Which configuration caused the IPS engine to generate this log?
Refer to the exhibit.

Given the exhibit, which two statements about FortiGate FGSP HA cluster behavior are correct? (Choose two.)
Which two statements about bounce address tagging and verification (BATV) on FortiMail are true? (Choose two.)