NSE7_CDS_AR-7.6 Exam Dumps - Fortinet NSE 7 - Public Cloud Security 7.6.4 Architect
Searching for workable clues to ace the Fortinet NSE7_CDS_AR-7.6 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s NSE7_CDS_AR-7.6 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
Refer to the exhibit.

You are managing an active-passive FortiGate HA cluster in AWS that was deployed using CloudFormation. You have created a change set to examine the effects of some proposed changes to the current infrastructure. The exhibit shows some sections of the change set.
What will happen if you apply these changes?
An organization is deploying FortiDevSec to enhance security for containerized applications, and they need to ensure containers are monitored for suspicious behavior at runtime.
Which FortiDevSec feature is best for detecting runtime threats?
Your DevOps team is evaluating different Infrastructure as Code (IaC) solutions for deploying complex Azure environments.
What is an advantage of choosing Azure Bicep over other IaC tools available?
Refer to the exhibit.
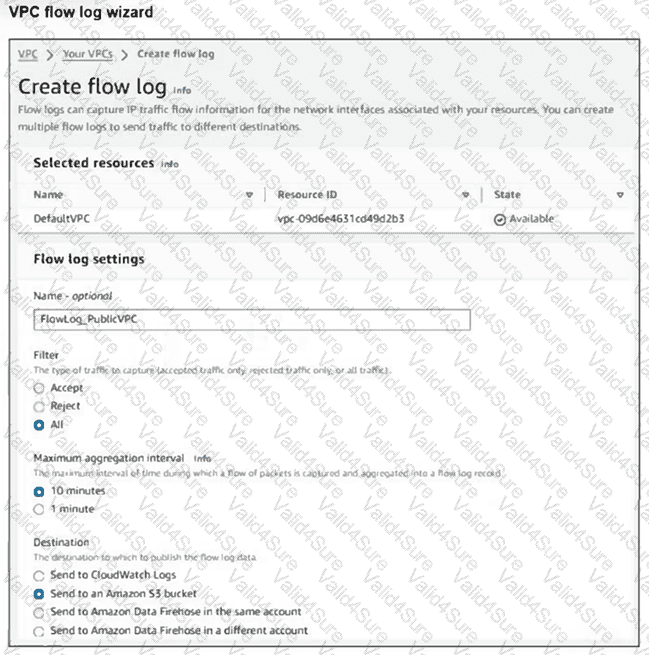
Your team notices an unusually high volume of traffic sourced at one of the organizations FortiGate EC2 instances. They create a flow log to obtain and analyze detailed information about this traffic. However, when they checked the log, they found that it included traffic that was not associated with the FortiGate instance in question.
What can they do to obtain the correct logs? (Choose one answer)
You are investigating an attack path for a top risky host. You notice that the Common Vulnerability Scoring System (CVSS) and the vulnerability impact scores are very high. However, the attack path severity for the top risky host itself is low. Which two pieces of contextualized information can help you understand why? (Choose two answers)
Exhibit.

In which type of FortiCNP insights can an administrator examine the findings triggered by this policy?
Refer to the exhibit.
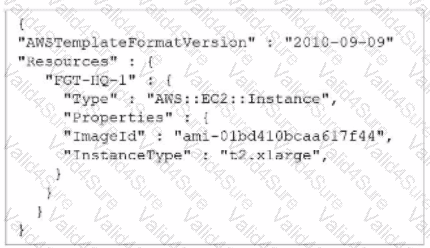
A senior administrator in a multinational organization needs to include a comment in the template shown in the exhibit to ensure that administrators from other regions change the Amazon Machine Image (AMI) ID to one that is valid in their location.
How can the administrator add the required comment in that section of the file?
Which statement about Transit Gateway (TGW) in Amazon Web Services (AWS) is true?