NS0-593 Exam Dumps - NetApp Certified Support Engineer ONTAP Specialist
Searching for workable clues to ace the Netapp NS0-593 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s NS0-593 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
Which two automation methods does NetApp ONTAP Select support? (Choose two.)
Your customer installed the shelf firmware for their NS224 shelf over a week ago, and the firmware has not upgraded on shelf 1 module B. The customer wants to know what the next steps would be to get the firmware upgraded after verifying that the shelf firmware is indeed loaded onto the system.
Which step would you perform to complete the firmware upgrade?
When an administrator tries to create a share for an existing volume named voll, the process fails with an error.

Referring to the exhibit, what Is the reason for the error?
Your customer added a new DS4246 shelf to their FAS2750 single-node system and created a new aggregate on the new shelf. Two weeks later, they log into Active IQ and discover the Medium Impact error shown below.
Shelves with both connections via the same SAS path detected
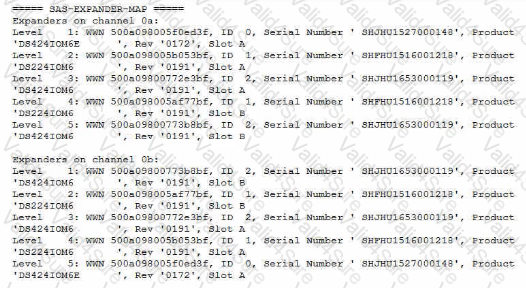
Referring to the exhibit, which statement is correct?
A user mentions that their home drive, that Is an export within a volume, is no longer allowing them to save files. The drive reports that it Is full, even though It shows that minimal data is written to it.
Which statement would explain this behavior?