NS0-527 Exam Dumps - NetApp Certified Implementation Engineer - Data Protection
Searching for workable clues to ace the Netapp NS0-527 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s NS0-527 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
A customer has developed a new application that uses Oracle with an AFF system to help track all of their shipping trucks around the world. The customer wants to ensure that application-consistent backups are offloaded to the cloud.
Inthis scenario, which two solutions enable the customer to satisfy these requirements? (Choose two.)
Click the Exhibit button.
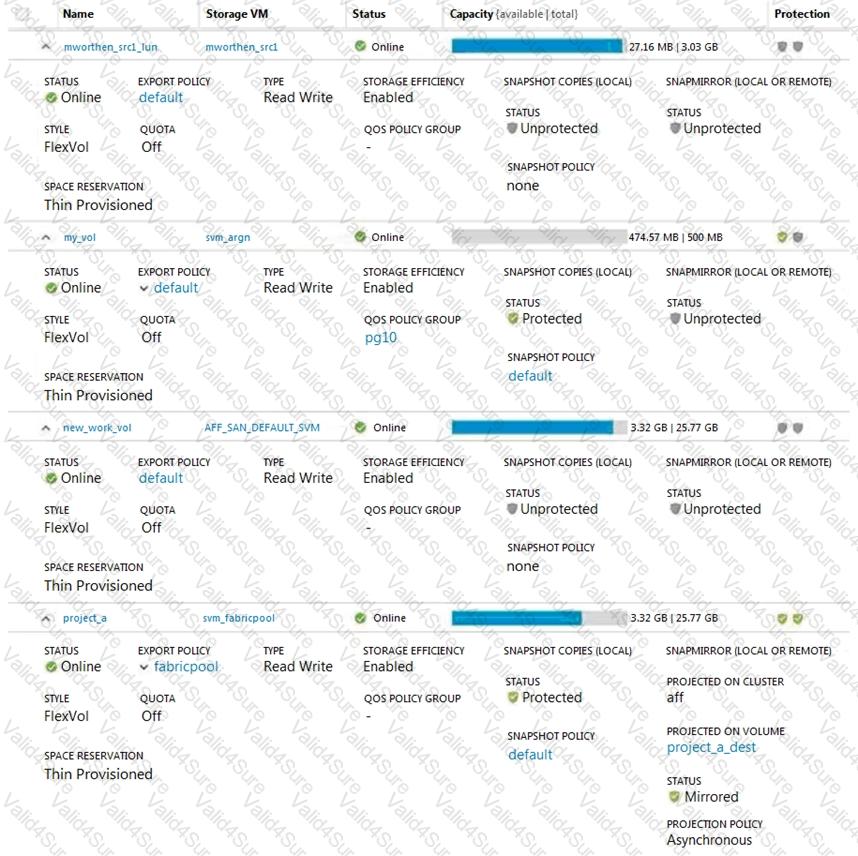
Referring to the exhibit, which volume has the highest level of protection assigned to it?
You have an environment with multiple database servers that are performing scheduled nightly dumps. These dumps vary in both the time to complete and the size of data produced. Youneed to ensure that there is always enough room in the volume for the data and that a nightly SnapMirror update does not take place until the database dump process is complete.
In this scenario, which NetApp tool ensures that this process is completed every night?
Your customer wants to implement SVM DR, but the customer is not certain whether theidentity-preserve parameter should be enabled. The customer explains that the source and destination clusters are in different network subnets.
In this scenario, which SVM DR solution should the customer use?
Click the Exhibit button.
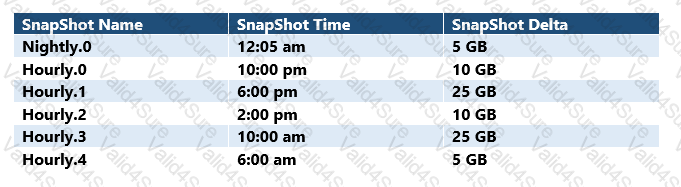
A client has a SnapMirror relationship between two sites that is scheduled to run once a day at 12:15 a.m. They have a network connection between two sites thatprovides 100 Mbps on bandwidth. By performing the backup at this time, they can maximize their bandwidth use.
Referring to the exhibit, how long does the SnapMirror update take to finish?