NCP-MCI-6.5 Exam Dumps - Nutanix Certified Professional - Multicloud Infrastructure (NCP-MCI) v6.5 exam
Searching for workable clues to ace the Nutanix NCP-MCI-6.5 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s NCP-MCI-6.5 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
An administrator is working with Nutanix Support and needs to provide logs for troubleshooting an issue. The cluster is located in a secure environment. Data such as IP addresses and VM names cannot be shared.
Which method should be used to anonymize the log data sent to Nutanix Support?
A)

B)
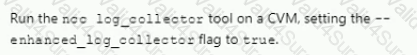
C)

D)

Which algorithm do snapshots and clones leverage to maximize efficiency and effectiveness?
Prism Central will be installed manually on an AHV cluster.
Which three disk images must be downloaded from the portal for the Prism Central VM? (Choose three.)