NCP-MCI-6.10 Exam Dumps - Nutanix Certified Professional - Multicloud Infrastructure (NCP-MCI v6.10)
Searching for workable clues to ace the Nutanix NCP-MCI-6.10 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s NCP-MCI-6.10 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
An administrator is responsible forresource planningand needs to plan forresiliencyof a10-node RF3 cluster. The cluster has100TB of storage.
How should the administrator plan for capacity in the event of future failures?
Refer to Exhibit:

An administrator notices the message shown in the exhibit when navigating to LCM from Prism Central.
Which action should the administrator take to update LCM to the latest version?
An administrator receives complaints about VM performance.
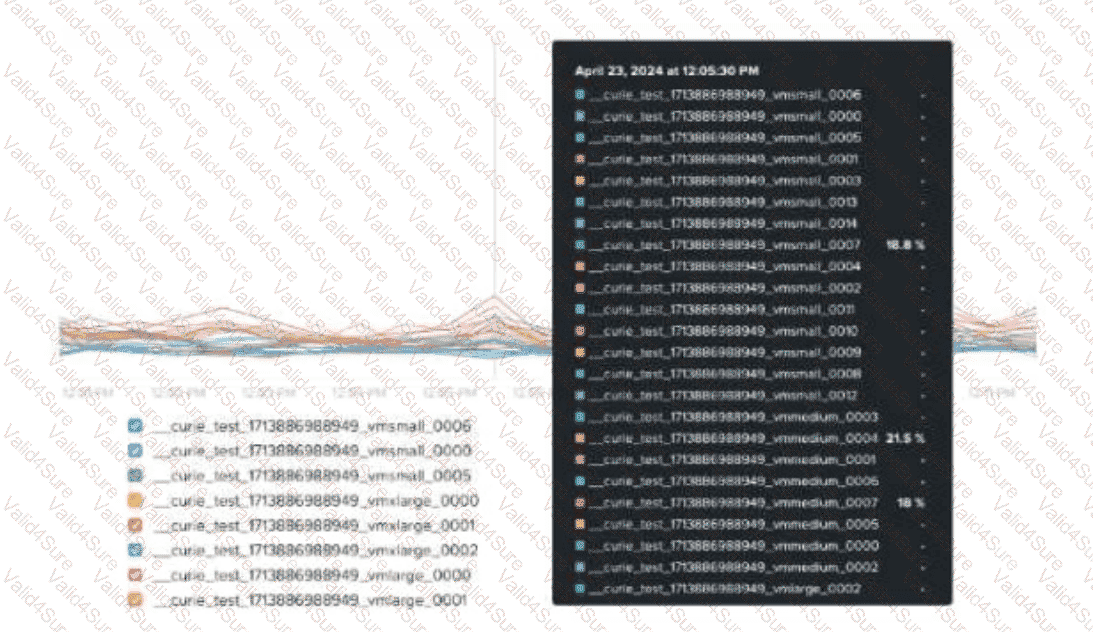
After reviewing theVM’s CPU Ready Timedata shown in the exhibit, which step should the administrator take to diagnose the issue further?
Which Nutanix product is used for automating application deployment across clouds?
An administrator needs to perform anLCM upgradeon anAHV host with GPUs.
What additional step is required before upgrading the host?
An administrator has been tasked with creating a new storage container named TestData. The TestData storage container must meet the following conditions:
• Replication Factor 1 (RF1)
• Inline Compression enabled
• Deduplication disabled
• Maximum storage capacity of 100 GiB
How should the administrator complete this task?
The administrator sees an alert stating that the “nutanix†user should not be allowed to SSH to the CVM using a password.
What should the administrator do to ensure the nutanix user can no longer SSH to a CVM using a password?