MS-900 Exam Dumps - Microsoft 365 Fundamentals
Searching for workable clues to ace the Microsoft MS-900 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s MS-900 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
Match each Microsoft 365 feature to its availability.
Instructions: To answer, drag the appropriate feature from the column on the left to its availability on the right. Each feature may be used once, more than once, or not at all.
NOTE:Each correct match is worth one point.

A company is evaluating Microsoft 365.
You need to identify the features of MicrosoftStream.
What are three features of Microsoft Stream? Each correct answer presents part of the solution.
Each correct selection is worth one point.
Instructions: For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Bach correct selection is worth one point.

Instructions: For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

You are the Microsoft 365 administrator for a company.
Your company wants lo team more about what happens if the availability the Microsoft Office 365 services are not met.
Where can you find this information?
You are a Microsoft 365 administrator for a company.
A customer submits a data subject request (DSR) to delete customerinformation in compliance with General Data Protection Regulation (GDPR). You must place legal holds on related data whenever possible.
You need to respond to the request by searching for the customer’s data in various Microsoft 365 tools.
How should yousearch for the data? To answer, drag the appropriate search methods to the correct Microsoft 365 applications. Each search method may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.

For each of the following statements, select Yes if the statement is true. Otherwise,select No.
NOTE:Each correct selection is worth one point.

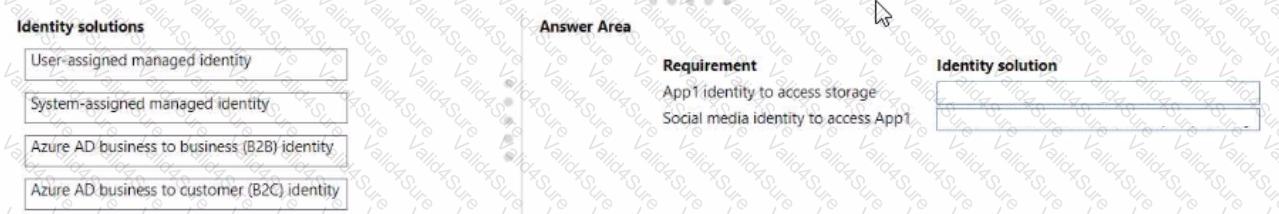
The company has the following requirements for apps in App1:
•Apps must use the same identity toaccess Azure Storage.
•Users outside the company must be able to access the apps by using their social media identity.
You need to identify the Azure Active Directory (Azure AD) identity solutions.
What should you use? To answer, drag the appropriate identity solution to the correct requirement. Each identity solution may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE Each correct selection is worth one point.