MS-102 Exam Dumps - Microsoft 365 Administrator Exam
Searching for workable clues to ace the Microsoft MS-102 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s MS-102 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
You have a Microsoft J65 E5 subscription.
You integrate Microsoft Defender for Endpoint with Microsoft Intune.
You need to ensure that devices automatically onboard to Defender for Endpoint when they are enrolled in Intune.
Solution: You enable co-management.
Does this meet the goal?
: 234
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 E5 subscription.
You create an account for a new security administrator named SecAdmin1.
You need to ensure that SecAdmin1 can manage Office 365 Advanced Threat Protection (ATP) settings and policies for Microsoft Teams, SharePoint, and OneDrive.
Solution: From the Azure Active Directory admin center, you assign SecAdmin1 the Teams Service Administrator role.
Does this meet the goal?
You have a Microsoft 365 E5 subscription that contains the groups shown in the following table.
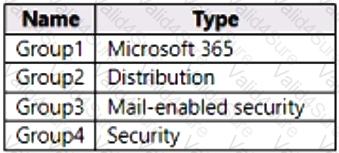
You plan to publish a sensitivity label named Label1.
To which groups can you publish Label1?
: 220 DRAG DROP
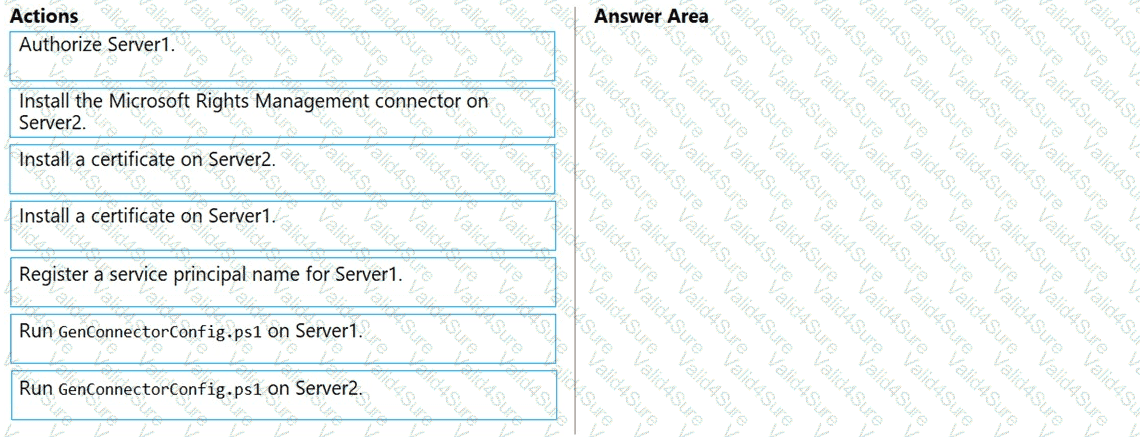
Your network contains an on-premises Active Directory domain that syncs to Azure Active Directory (Azure AD). The domain contains the servers shown in the following table.

You use Azure Information Protection.
You need to ensure that you can apply Azure Information Protection labels to the file stores on Server1.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
You have a Microsoft 365 E5 subscription that contains a user named User1. You create an anti-phishing policy named Policy! that has the following settings:
• Include these users, groups and domains: User1
• Phishing email threshold: 3 - More Aggressive
User1 receives the email messages shown in the following table.
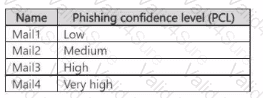
Which messages are phishing email?
You have a Microsoft 365 subscription.
You have the retention policies shown in the following table.
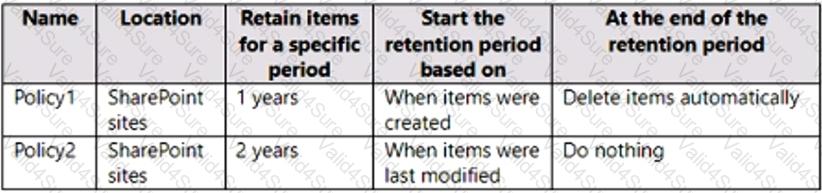
Both policies are applied to a Microsoft SharePoint site named Site1 that contains a file named File1.docx.
File1.docx was created on January 1, 2022 and last modified on January 31,2022. The file was NOT modified again.
When will File1.docx be deleted automatically?
: 221
You have a Microsoft 365 E5 subscription.
Users have the devices shown in the following table.
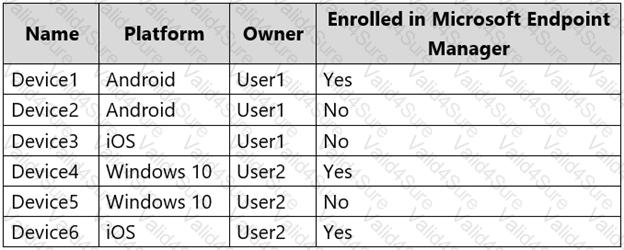
On which devices can you manage apps by using app configuration policies in Microsoft Endpoint Manager?
Your company has multiple offices.
You have a Microsoft 365 E5 tenant that uses Microsoft Intune for device management. Each office has a local administrator.
You need to ensure that the local administrators can manage only the devices in their respective office.
What should you use?