JN0-636 Exam Dumps - Security, Professional (JNCIP-SEC)
Searching for workable clues to ace the Juniper JN0-636 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s JN0-636 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
Exhibit
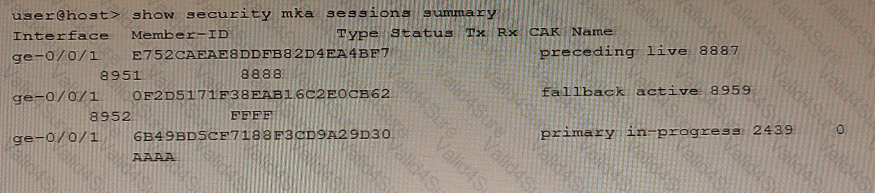
Referring to the exhibit, which two statements are true about the CAK status for the CAK named "FFFP"? (Choose two.)
Regarding IPsec CoS-based VPNs, what is the number of IPsec SAs associated with a peer based upon?
you must find an infected host and where the a􀆩ack came from using the Juniper ATP Cloud. Which two monitor workspaces will return the requested information? (Choose Two)
Exhibit
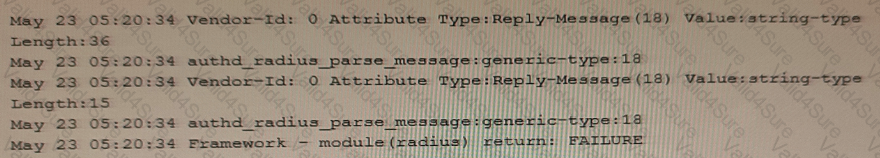
You configure a traceoptions file called radius on your returns the output shown in the exhibit
What is the source of the problem?
Exhibit
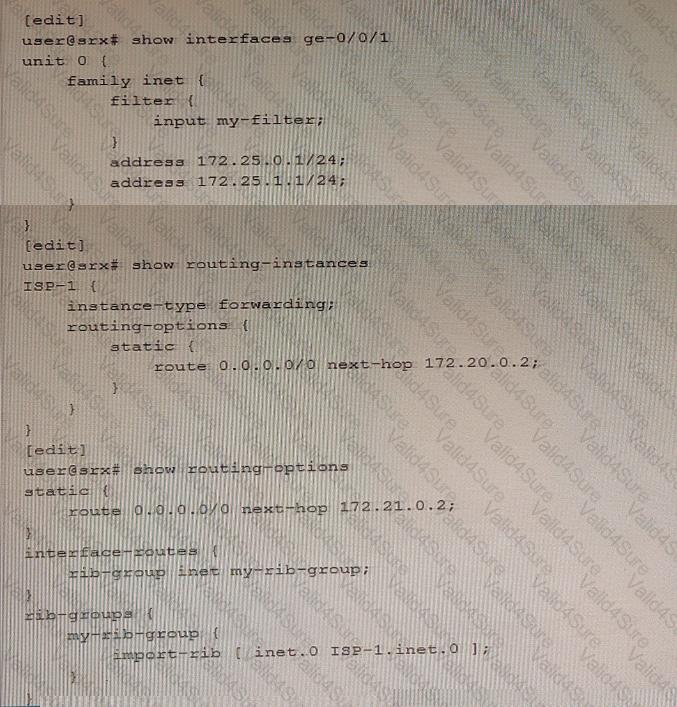
You are implementing filter-based forwarding to send traffic from the 172.25.0.0/24 network through ISP-1 while sending all other traffic through your connection to ISP-2. Your ge-0/0/1 interface connects to two networks, including the 172.25.0.0/24 network. You have implemented the configuration shown in the exhibit. The traffic from the 172.25.0.0/24 network is being forwarded as expected to 172.20.0.2, however traffic from the other network (172.25.1.0/24) is not being forwarded to the upstream 172.21.0.2 neighbor.
In this scenario, which action will solve this problem?
SRX Series device enrollment with Policy Enforcer fails To debug further, the user issues the following command show configuration services security—intelligence url
https : //cloudfeeds . argon . juniperaecurity . net/api/manifeat. xml
and receives the following output:
What is the problem in this scenario?
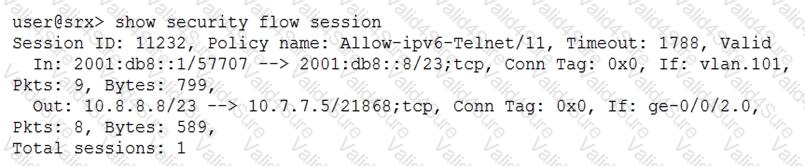
Exhibit
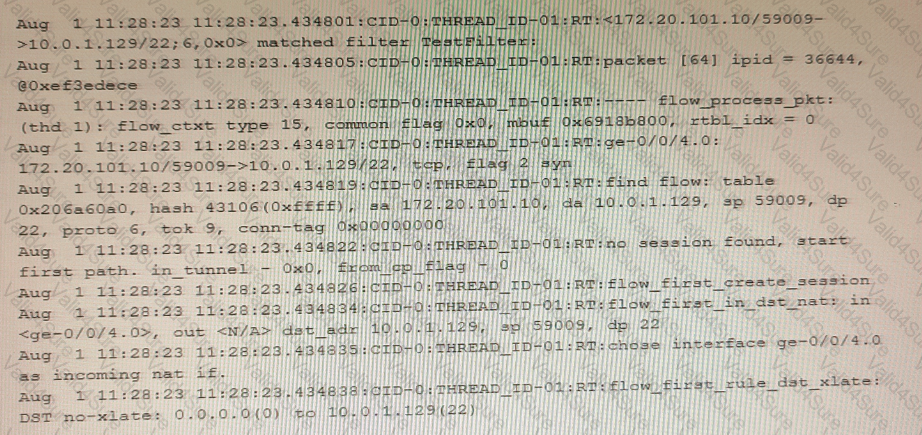
The exhibit shows a snippet of a security flow trace.
In this scenario, which two statements are correct? (Choose two.)