JN0-232 Exam Dumps - Security, Associate (JNCIA-SEC)
Searching for workable clues to ace the Juniper JN0-232 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s JN0-232 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
You have a situation where legitimate traffic is incorrectly identified as malicious by your screen options.
In this scenario, what should you do?
Click the Exhibit button.
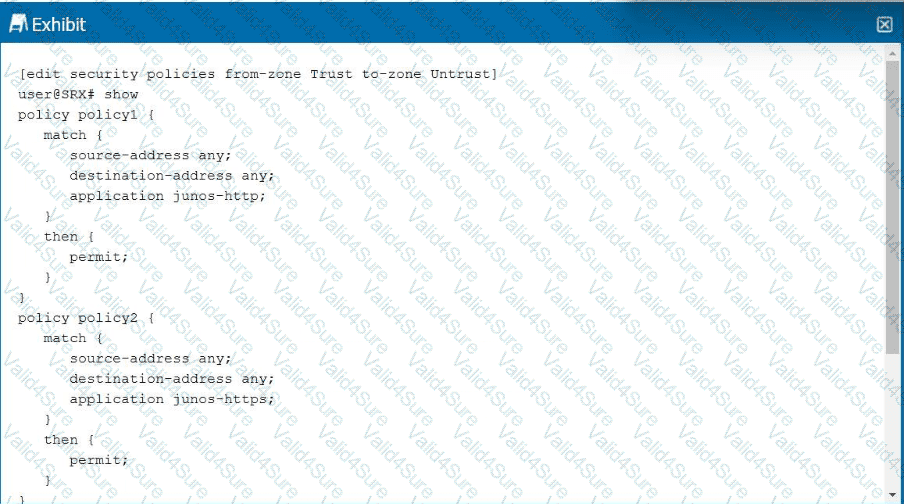

Referring to the exhibit, which statement is correct?
Which statement is correct about capturing transit packets on an SRX Series Firewall?
What is the purpose of assigning logical interfaces to separate security zones in Junos OS?
What are two ways that an SRX Series device identifies content? (Choose two.)
You need to capture control plane traffic on a high-end SRX Series device.
How would you accomplish this task?
