H13-511_V5.5 Exam Dumps - HCIA-Cloud Computing V5.5 Exam
Searching for workable clues to ace the Huawei H13-511_V5.5 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s H13-511_V5.5 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
To enhance the security of user desktops, FusionAccess supports diverse access management policies. Which of the following statements about access management policies are true?
When a user VM uses a USB device, FusionAccess defaults to "USB Port Redirection". If the device is still unavailable, the"Device Redirection"policy can be configured.
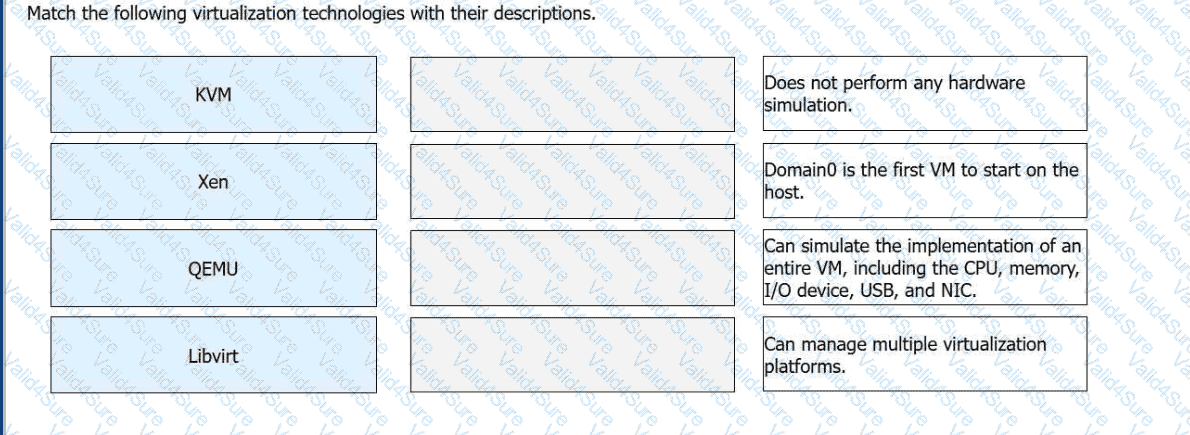
Which of the following statements is false about concepts of virtualization?
Generally, a subnet mask is used together with an IP address. The 0s in the binary value represent the network portion of an IP address, and the 1s represent the host portion.
In virtualization, KVM and Xen are typical hardware-assisted virtualization technologies. They implement virtualization based on kernel modules in the operating system.