FCSS_SASE_AD-25 Exam Dumps - FCSS - FortiSASE 25 Administrator
Searching for workable clues to ace the Fortinet FCSS_SASE_AD-25 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s FCSS_SASE_AD-25 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
In a FortiSASE secure web gateway (SWG) deployment, which two features protect against web-based threats? (Choose two.)
Refer to the exhibits.
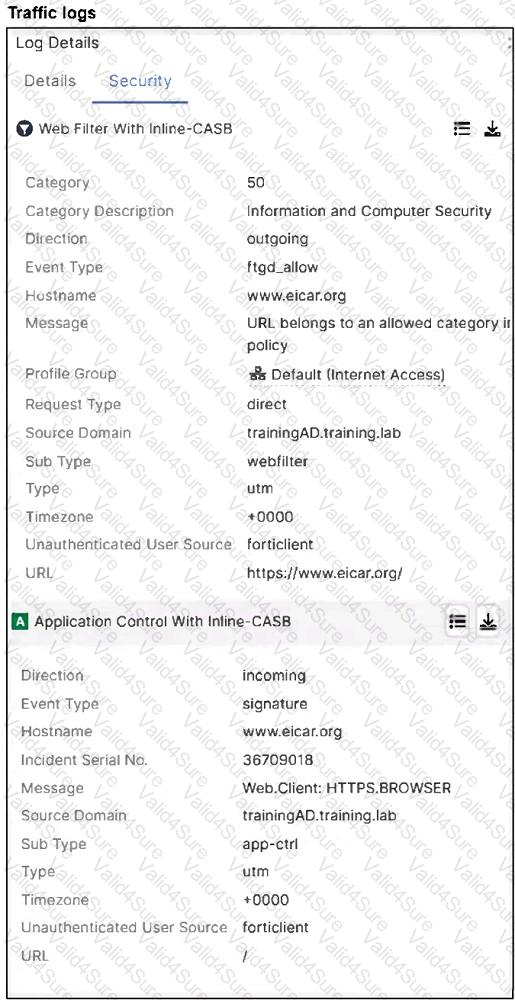
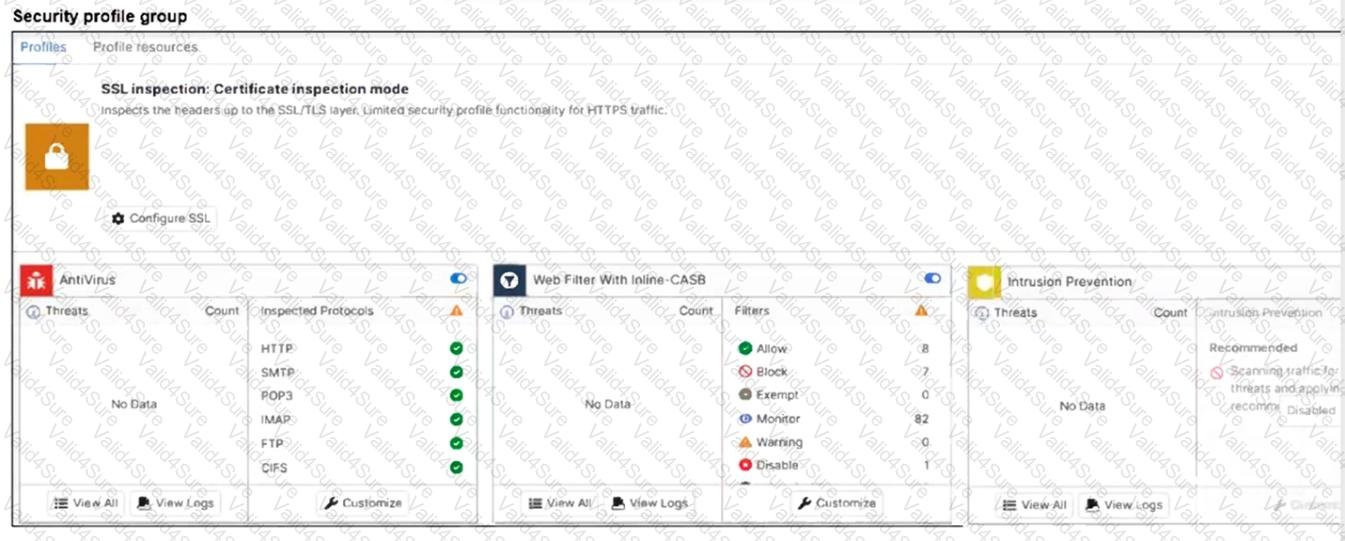
A FortiSASE administrator has configured an antivirus profile in the security profile group and applied it to the internet access policy. Remote users are still able to download the eicar.com-zip file from https://eicar.org.
Which configuration on FortiSASE is allowing users to perform the download?
In the Secure Private Access (SPA) use case, which two FortiSASE features facilitate access to corporate applications? (Choose two.)
When accessing the FortiSASE portal for the first time, an administrator must select data center locations for which three FortiSASE components? (Choose three.)
What happens to the logs on FortiSASE that are older than the configured log retention period?
Which information can an administrator monitor using reports generated on FortiSASE?